HTTPS is Secure (Except When it’s Not)
Category
Awareness, Cybersecurity Fundamentals
Risk Level
“What are HTTP and HTTPS? Are they the same? ”
At the beginning of the internet’s popularity, HTTP (Hypertext Transfer Protocol), was used to transmit data between clients (web browsers) and web servers. However, any data transmitted between the client and server was not protected. As internet culture became increasingly popular around the world and brought with it an urgent need to protect sensitive data from malicious actors, HTTPS was born. HTTPS stands for Secure Hypertext Transfer Protocol. It is HTTP with security features to protect sensitive information using SSL/TLS protocols. The padlock symbol that shows at the top of your browser is a visual sign that the data transmission taking place between the browser and the server is safe and encrypted.
“How are SSL and TLS involved in this?”
SSL stands for Secure Sockets Layer, and TLS stands for Transport Layer Security. The SSL protocol was first introduced to HTTP to serve the security portion of the client and server data transfer relationship. SSL was established using cryptographic technology to widen client and server security in the early internet era. The main benefit that came with the invention of the SSL protocol is the digital certificate authentication process which involves the client and server initiating a preliminary procedure together by exchanging crucial information such as a public key, session ID, digital certificate, etc. This information is necessary to set up a secure and encrypted connection, and to validate that it is a trusted source. With this protocol in place, it prevents hackers from viewing your information as it is transmitted across the internet because it’s in an encrypted form.
“Got it. But what do I need to know about SSL and TLS?”
In the early days, SSL was widely used. The first version of SSL, SSL v1.0, was never publicly released due to numerous security vulnerabilities. The first ever SSL version released to the public was SSL v2.0 and later SSL v3.0 which included updated security features. Eventually, a new method was created called TLS, which was introduced with enhanced security features but built on the core technology of SSL.
Many TLS versions have been introduced since TLS 1.0, and nowadays, the minimum recommended TLS version is TLS 1.2 and above since all of the previous versions (including SSL) are now considered vulnerable. TLS 1.3 is the latest version in the TLS series and provides the highest security and performance among all the other versions.
“OK! I see the padlock icon and HTTPS in the browser. Does it mean it is secure?”
Remember at the beginning of the article when we mentioned that HTTPS is not secure - or at least not always? While using a secure version of HTTPS to protect the transmission of data between your web browser, like Google Chrome and Firefox, and the rest of the internet is important, it’s not everything. HTTPS can act like a tunnel to help protect your sensitive data, such as personal information, financial information, and individual health records, etc., from being hijacked in transit, but it’s important to understand how it works, and its limits.
HTTPS can only do so much, and we need to pay attention to who is hosting the web server on the other side and make sure it is a legitimate party. If a malicious actor is hosting the web server, it makes no difference if you’re using HTTPS - the actor can still get access to your sensitive data.
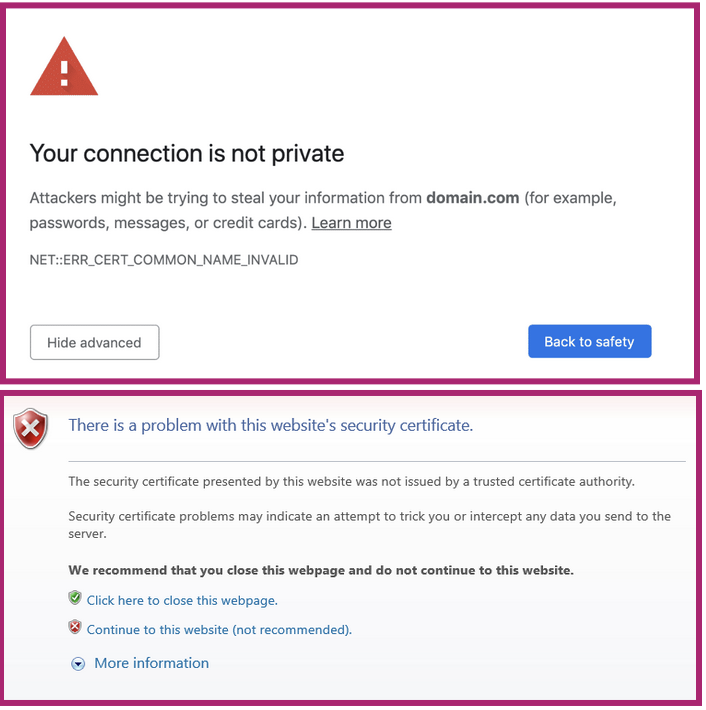
Therefore, it is crucial to understand and practice the appropriate preventive measures. Always stop and take the time to verify that the website to which you provide critical information is legitimate. Here’s a great Google tool you can use to determine if the URL is safe or harmful. Additionally, if you attempt to navigate to the site and your browser warns you that a certificate associated with the site is not trusted or that your connection is not private (your browser may say “Not Secure” or show a lock symbol with a red “X” on it), it is safer to not continue than to bypass the warning. That warning is indicative of either a misconfigured SSL/TLS certificate, which may be harmless but fails to provide full protection and should still be avoided, or a malicious site attempting to pass as secure by using HTTPS vs. HTTP to aid in the appearance of legitimacy. In either case, vigilance is required and you should only continue if you know and trust the server on the other end and are sure your connection is secure and not being man-in-the-middle attacked or hijacked.
How an untrusted certificate warning might look on a browser
In most phishing attempts, the malicious attacker sends the URL by SMS, email, or other means. Instead of clicking on the URL, go directly to the source (i.e., open your own browser window and navigate to the website or service using a typed or searched for URL you know is legitimate) to prevent becoming a hacker or scammer's next victim. If you are in the workplace and have doubts about any suspicious link, report it to your IT or cybersecurity team. Just remember that while HTTPS is great in some ways, it is only part of the picture.
"What do I do now?"
We know cybersecurity topics can be complicated sometimes. Our team of cybersecurity experts at Hive Systems is always here to provide support, advice, and products to help make cybersecurity approachable.. Contact us today!





It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. How did we make this table? Want to download a copy? Read on!