
If corporate America, government entities, and hospitals weren't enough, now ransomware developers are attacking Golf!
According to a report from GolfWeek, computers at the PGA of America’s offices have been infected with ransomware. The victims learned they were infected on Tuesday when ransom notes started appearing on their screen.
"Your network has been penetrated," the ransom note read according to Golfweek's article. "All files on each host in the network have been encrypted with a strong algorythm [sic]."
Based on these strings and the misspelling of "algorithm", PGA of America was most likely infected with the BitPaymer ransomware. This is the same type of ransomware that recently hit the Alaskan town of Matanuska-Susitna and forced them to use typewriters for a week.
BitPaymer becoming more active?
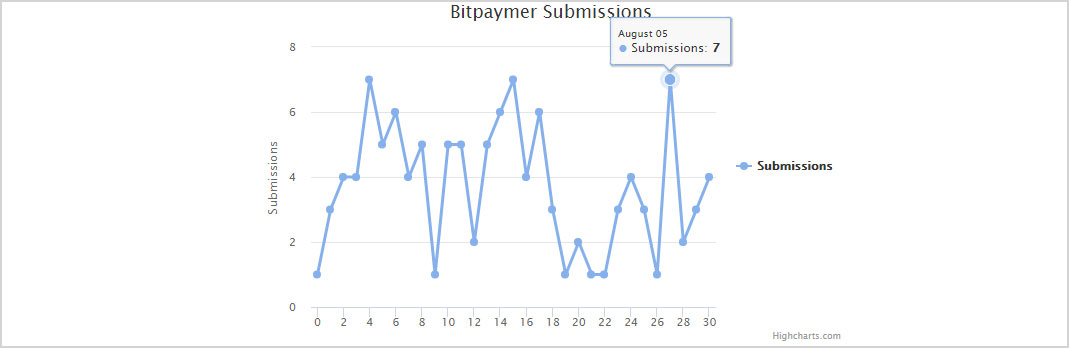
As already stated, based on the reported ransom note, PGA of America was most likely targeted by the BitPaymer Ransomware. BitPaymer has been around for a while, but typically keeps a low profile. There has been some moderate activity, though, with Bitpaymer over the last few weeks though as shown by the ID Ransomware chart below.
Like SamSam, BitPaymer tends to target organizations by hacking into Remote Desktop Services connected to the Internet. Once inside a network, they traverse through it and encrypt every computer they can get access to.
Recent variants have been appending the .locked extension to encrypted files and dropping ransom notes of the same name as the encrypted files but with ".readme_txt" appended to it. For example, an encrypted file called test.jpg would also have a ransom note named test.jpg.readme_txt.
You can see an example ransom note for the BitPaymer Ransomware below. Notice the strings in the example below match those mentioned in the GolfWeek article.
Your network has been penetrated.
All files on each host in the network have been encrypted with a strong algorythm.
Backups were either encrypted or deleted or backup disks were formatted.
We exclusively have decryption software for your situation.
DO NOT RESET OR SHUTDOWN - files may be damaged.
DO NOT RENAME the encrypted files.
DO NOT MOVE the encrypted files.
This may lead to the impossibility of recovery of the certain files.
To get info(pay-to-decrypt your files) contact us at:
[first_contact_email]
or
[second_contact_email]
BTC wallet:
[bitcoin_address]
To confirm our honest intentions.
Send 2 different random files and you will get it decrypted.
It can be from different computers on your network to be sure we decrypts everything.
Files should have .LOCK extension of each included.
2 files we unlock for free.
BitPaymer is also known to charge very large ransom amounts to decrypt computers. For example, one BitPaymer infection in the past asked for 53 bitcoins to decrypt an entire network.
Unfortunately, BitPaymer is a secure ransomware, which means either PGA of America is going to have to restore from backup or pay a hefty ransom payment.
Update 8/9/18: Article updated to clarify that the PGA of America's computers were infected and not PGA Tour.


Comments
DCorderoTOUR - 5 years ago
Lawrence. Huge clarification. The PGA of America (not the PGA TOUR) was hacked. The PGA of America is an entirely different organization, based in South Florida. The PGA TOUR, is in Ponte Vedra Beach, FL and WAS NOT hacked. Please remove our logo from the picture. Thank you!
Lawrence Abrams - 5 years ago
Apologies. Article updated and images changed.
DCorderoTOUR - 5 years ago
Thank you!
woody188 - 5 years ago
These RDP ones are the worst. We've found they are often used to HIDE what has been TAKEN so while you are busy dealing with the ransomware, they are selling your data or using it to penetrate your partners and vendors.