
Smart water irrigation systems deployed across a city, region, or even a country, can be hijacked by nefarious threat actors who could cause a mass water crisis by forcing these systems to consume more water than usual.
This is the conclusion and warning of recent research presented by a team of Israeli academics at a security conference in the US.
Infrastructure attacks on water supply systems
The research team argues that threat actors could identify vulnerabilities in popular smart water irrigation systems left connected to the Internet and use them to assemble botnets that exploit these flaws.
Researchers argue that threat actors could synchronize these irrigation systems to start at the same time and trigger a mass consumption of local water resources.
Such attacks, they say, could lead to the emptying of local emergency water reservoirs, and even to water utility companies shutting down water supply in extreme cases.
As part of their research, to determine the feasibility of such attacks, the team of academics has identified vulnerabilities in smart water irrigation systems from popular vendors such as BlueSpray, GreenIQ, and RainMachine, proving that such flaws exist and can be easily found. All vulnerabilities were reported to their respective vendors.

The research team, all from the Ben-Gurion University of the Negev (BGU), says that attackers don't necessarily need to infect the water irrigation system directly.
In an email conversation with Bleeping Computer, Ben Nassi, a BGU Ph.D. student and former Google employee, said that attackers can also infect devices on the same network (LAN) as the irrigation system.
This can be local routers, computers, WiFi hotspots, and other IoT devices. The attacker can use these initial point of entry as a relay point for scans that look for smart irrigation systems, and then exploit them via known vulnerabilities.
This means that smart irrigation systems don't need to be connected to the Internet directly, making the attack surface for these devices even larger.
IoT DDoS botnets can help attackers
Furthermore, Nassi told us that an attacker doesn't have to necessarily infect devices in the first place, as he could simply rent one of the many DDoS-for-hire botnets and use the bots part of that botnet to scan for smart irrigation systems on local networks. Malicious ads (malvertising) on popular sites could also help attackers relay malicious code to internal LANs.
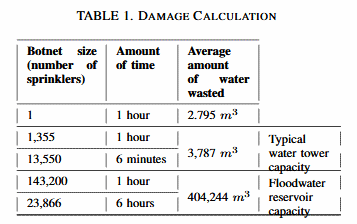
Nassi and his colleagues have even calculated how large the botnet needs to be for certain attacks.
"A standard water tower can be emptied in an hour using a botnet of 1,355 sprinklers," Nassi et. all wrote in their whitepaper. "A flood water reservoir can be emptied overnight using a botnet of 23,866 sprinklers."
Ideal type of attack for nation-state threat actors
But while using bots from DDoS botnets seems a complicated process, Nassi described this entire exploitation scenario as easily doable, and nothing that's above the complexity level of what's currently happening on the IoT malware scene where we've seen much more complicated attacks, such as VPNFilter.
The biggest danger, he argues, is from nation-state actors.
"I believe that such an attack will appear in the wild within the next years if the entire eco-system ignores our conclusions," Nassi told Bleeping Computer.
Main targets include agricultural areas where a water shortage could damage crops and desert areas where water shortages can be caused with ease due to the limited water supply.
"Even if urban water services able to detect such an [water reserve draining] attack, the only thing that they can do to against it is to stop providing water," Nassi said via email. "By doing so they will prevent people from obtaining water, so they will create a new problem because preventing people from obtaining water is a bigger problem."
In other words, even if water utility companies intervene at surge points to stop water supply and prevent reserve depletion, the attack will still be successful because water supply would have been stopped for consumers regardless if a reservoir was emptied or not, making this a double-edged sword in the hands of malicious threat actors.
More details about Nassi et all's research are available in a whitepaper entitled "Piping Botnet - Turning Green Technology into a Water Disaster." This researcher was also presented at the IoT Village at the DEF CON 26 security conference held in Las Vegas last week.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now