A new variant of the BTCWare ransomware was discovered by Michael Gillespie, that appends the .[email]-id-id.shadow extension to encrypted files. The BTCWare family of ransomware infections targets its victims by hacking into poorly protected remote desktop services and manually installing the ransomware.
Below is a brief summary of changes in this new Shadow btcware ransomware variant.
What's New in the Shadow Ransomware BTCWare Variant
Not much has changed with this new variant other than the email addresses a victim should contact the developer with and the extension appended to encrypted files. In this version, the contact email address is now paydayz@cock.li, which is listed in the ransom note below.
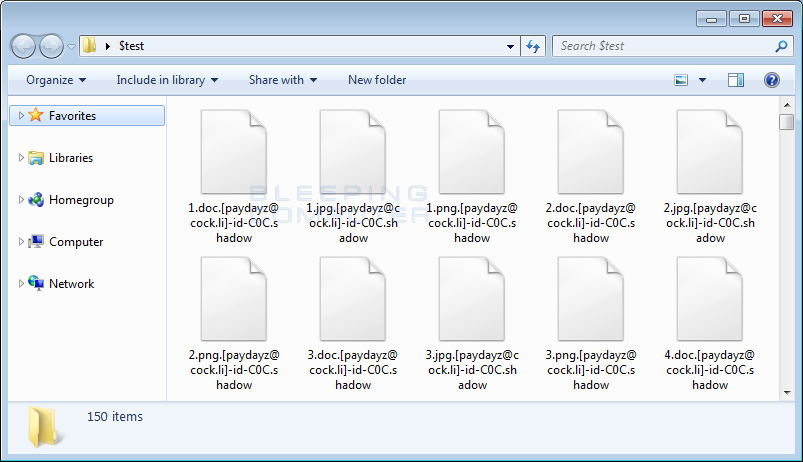
The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .[email]-id-[id].shadow extension to encrypted file's name. For example, the file test.jpg was encrypted and renamed to test.jpg.[paydayz@cock.li]-id-C0C.shadow.
You can see an example of an encrypted folder below.
If any new information or methods to decrypt the files becomes available, we will be sure to update this article.
How to protect yourself from the Shadow BTCWare Ransomware
In order to protect yourself from ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics.
Last, but not least, make sure you practice the following security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed that uses behavioral detections or white list technology. White listing can be a pain to train, but if your willing to stock with it, could have the biggest payoffs.
- Use hard passwords and never reuse the same password at multiple sites.
As this particular variant targets open Remote Desktop services it is important that you do not connect a remote desktop server directly to the Internet. Instead you should require a user to VPN into your network first to be able to connect to the remote desktop server.
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.
IOCs
File Hashes:
SHA256: ebcc0fa9c078ed66aa49f4b4eafa97218e121733a6f700fde33c7304da199108
Filenames associated with the Shadow Ransomware Variant:
%AppData%\payday.hta
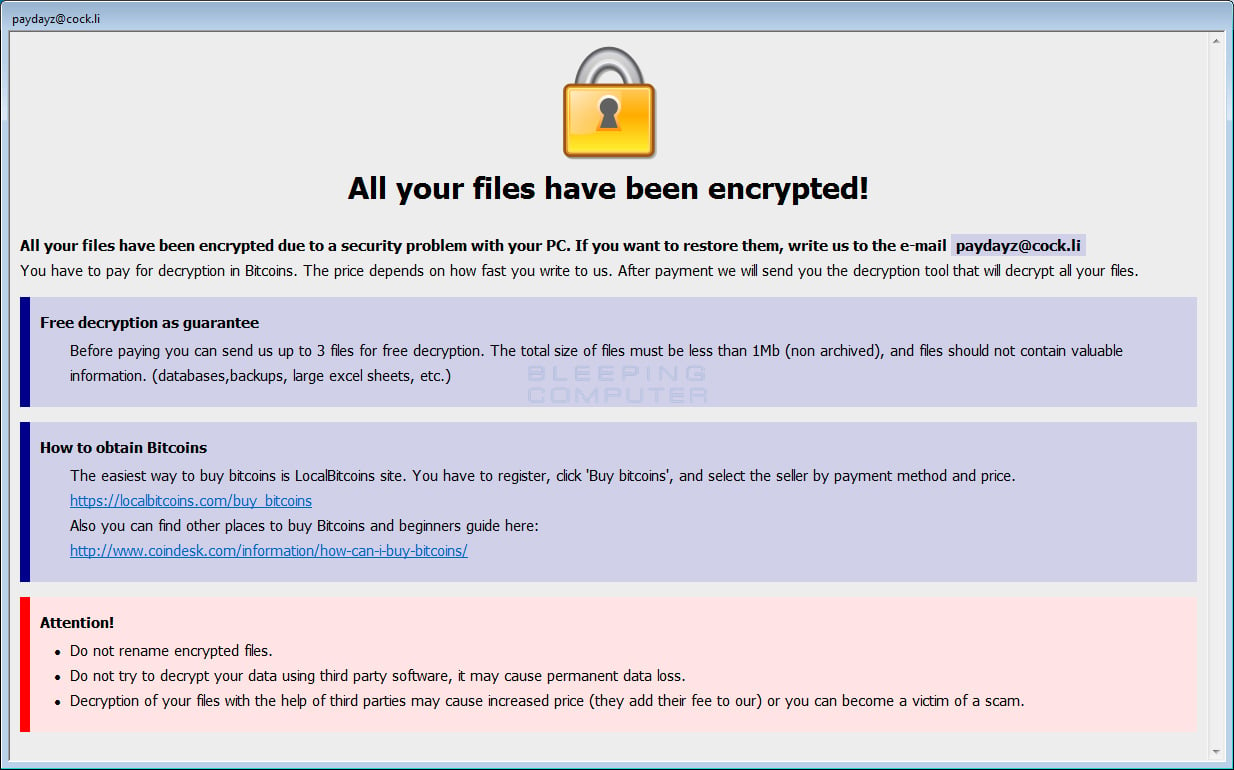
Shadow BTCWare Ransomware Ransom Note Text:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail paydayz@cock.li
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Emails Associated with the Shadow Ransomware:
paydayz@cock.li


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now