iPhone, iPad lock screen bypass fixed, but 34 days too late

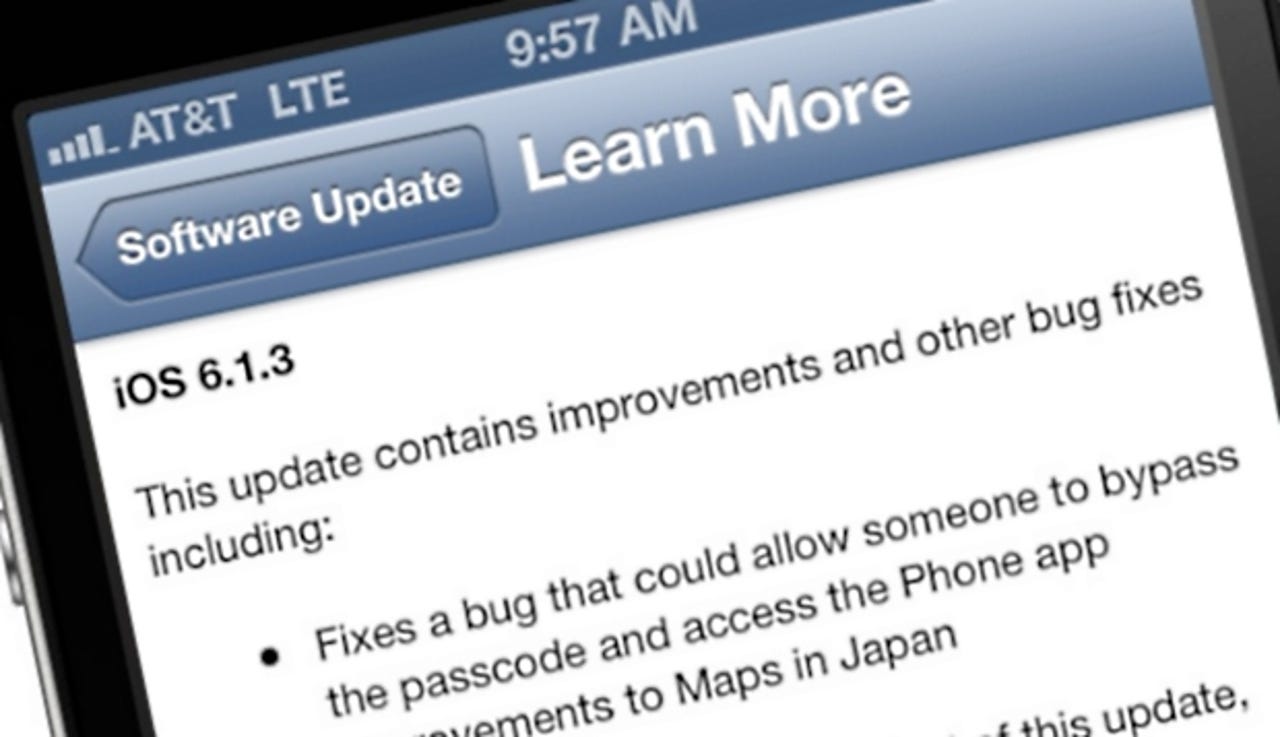
It took more than a month for Apple to fix a flaw with iPhone and iPad lock screens that allowed hackers to easily break into a user's iOS 6.1-powered device.
In just a few button presses and key taps, it was possible to bypass the four-digit lock screen and gain full access to rifle through parts of their iOS 6.1-powered device — which, by the way, would have been a significantly high proportion of all devices — not limited to photos, server-stored emails and contacts, voicemail and other private data.
Engage the enterprise panic switches. Your bring-your-own-device (BYOD) staff using their iPhones and iPads alike have been taking their devices home (or left on the train, at a bus stop, or had their devices stolen) whereby the ripple effect could result in the leaking of sensitive corporate data — or worse, citizen data — considering a rise in government employees using Apple products.
And yet it took 34 days, from February 14 to March 19, for one of the world's most advanced technology companies by staff and by wealth to fix the very front door, the first line of defense against unauthorized users, to its customers' phones and tablets.
During that time, Apple issued another update in form of iOS 6.1.2 that fixed a nasty Exchange Server-related bug that churned up servers with "excessive logging" problems. But there was no sight of a lock screen fix even then.
Apple said in a statement at the time that it was "aware of this issue, and will deliver a fix in a future software update." It did not, however, give a time frame in which it would do so, leaving many without a clue as to what their own employees should do to mitigate any security-related circumstances.
Apple, in true fashion, stayed mum. Not a word beyond the statement. No idea on when the problem would be fixed, or how to at least reduce the risk of a lock screen bypass.
The company also said that it "takes user security very seriously."
Again, that's five weeks, or more than one month until a fix was finally pushed out of the doors at Cupertino.
Whatever spin story you want to use, this is a pretty poor effort on Apple's part. Sure enough, many enterprises would have reacted to this security flaw by simply engaging a server-side policy that forced a stronger alphanumeric password on each connected device. (Besides which, that should be a standard in any enterprise, but that's missing the point.)
We should not forget, however, that Samsung also experienced a very similar flaw, in which hackers are able to bypass — albeit momentarily — the Android 4.1.2 lock screen on some Galaxy devices
Samsung, for the record, didn't even respond to a request for comment, putting it very much in the same position as Apple.
The bottom line to this is that the lock screen (on any device, in fact) is the very first defense against hackers. Most hackers, for the record, actually require a little skill to break into a device. But this was a wide-open flaw that allowed practically anybody — perhaps those sans fingers — to bypass the most basic of protections.
It was a massive a data protection and privacy risk that went unpatched for too long.