
The Guardian's SecureDrop whistleblower submission site was targeted with a phishing page that attempted to harvest the unique "codenames" for sources who submitted information using the service. In addition, this phishing page promoted an Android app that allowed attackers to perform a variety of malicious activity on a victim's device.
SecureDrop is a service that media organizations can install on the Tor network in order to allow whistleblowers or sources to submit anonymous information to journalists. For example, below is the legitimate Tor SecureDrop site for The Guardian hosted at the 33y6fjyhs3phzfjj.onion address.
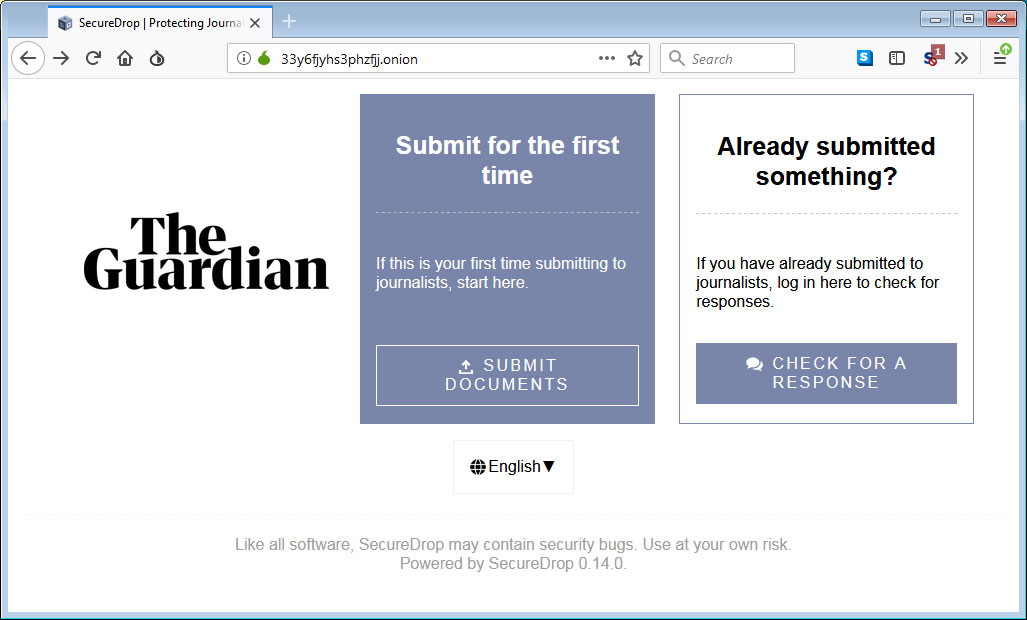
When a source wishes to submit confidential information to the media outlet's journalists, they receive a codename that can then be used for further communication. This codename is meant to be private as anyone who knows it can see the source's past communications with journalists.
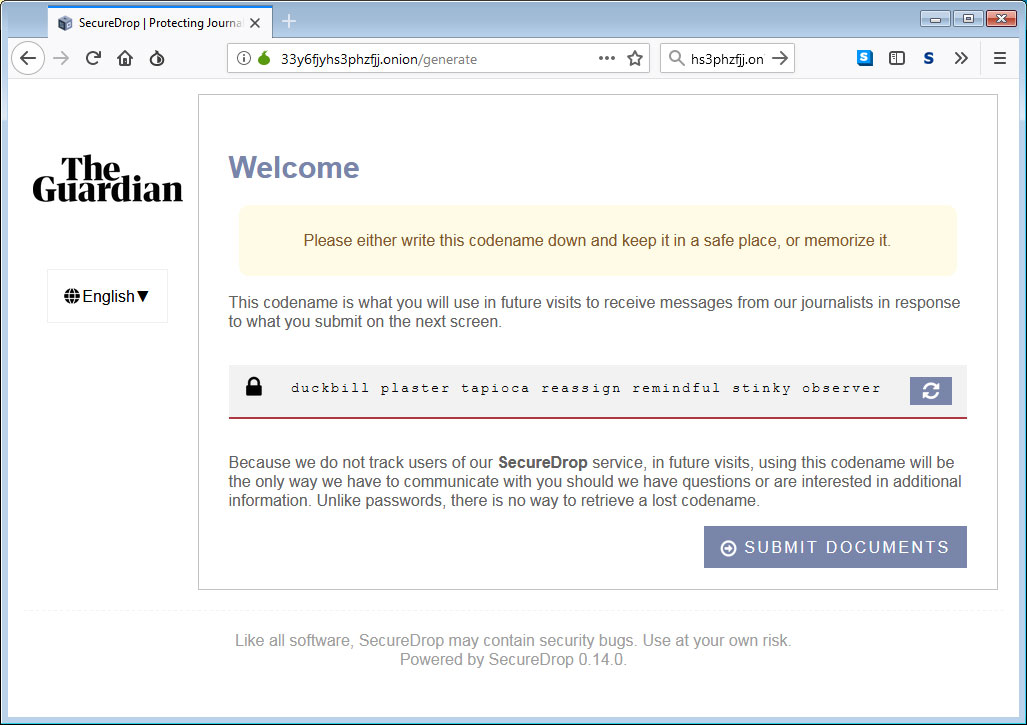
SecureDrop phishing site for The Guardian
Over the weekend, darknet and underground market researcher Sh1ttyKids, discovered a phishing page that impersonated the SecureDrop site for The Guardian.
As you can see below, this page is almost identical to the real SecureDrop site, but is instead a phishing page that can be used to harvest a sources's codename.

Once the attackers gain access to a source's codename, they can then login with it on The Guardian's real SecureDrop site and impersonate the source and steal information and communications.
Sh1ttyKids told BleepingComputer that soon after he tweeted about the phishing site it was taken offline. He did not know, though, whether the site was taken offline by The Guardian's security team, who were notified, or the attackers.
BleepingComputer has reached out to The Guardian with questions related to the page being taken down.
Even though the page is now down, unfortunately the harm may have already been done as not only was this phishing site harvesting SecureDrop codenames, but was also pushing a malicious Android app that could allow the attackers to monitor anyone who installed it.
Malicious Android app
In addition to harvesting codenames, the phishing page was also promoting an Android app that could "hide your location".

While this phishing page is no longer available, security researcher Robert Baptiste was able to download and share the app before it became unavailable.
After BleepingComputer decompiled the app, we can see that it has a ton of permissions that can be used to perform RAT-like behavior such as monitoring a victim's activity, location, calls, texts, stealing data, and executing commands.

From BleepingComputer's analysis, the app will connect to its command & control server to retrieve a command to execute. These commands include malicious activity such as:
- Create system alerts
- Blocking the screen from automatically locking
- Make phone calls
- Capture voice calls
- Read contacts
- Read, write, and send SMS texts
- Access a user's location
- Read and write the call log
- Access the device's storage and camera
- Change WiFi state and scan for available networks
- Access the clipboard
- Take pictures
- Get a list of installed apps
- Upload, download, and delete files
ESET malware researcher Lukas Stefanko took at a quick look at the app for BleepingComputer and confirmed our findings that it performs RAT-like behavior.
"The app is remotely controled malware and will execute commands sent by the server. It can also get text from notifications, send images from the gallery, and take screenshots if the device is rooted."
In addition, to being able to execute the above actions, the app will also send back information about the device to the attackers. Some of this information could be useful in attempts to perform a SIM hijack.

Baptiste stated that the app would send the gathered information back to a command & control server located at 213.188.152.96. This IP address has a history of malicious activity for a variety of different malware.
If a user has installed this app on their phone, it should be assumed that their calls, texts, and data have been compromised and act accordingly.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now