
Malware authors are using an NSA hacking tool to infect Windows computers with a new cryptocurrency miner. Detected under the generic name of Trojan.BtcMine.1259, this trojan was first spotted last week by Russian antivirus vendor Dr.Web.
The trojan uses an NSA implant called DOUBLEPULSAR to infect computers that run unsecured SMB services. This implant (NSA term for malware) is a simple backdoor that allows attackers to execute code on the infected machines.
The miscreants behind these attacks use DOUBLEPULSAR to download a generic malware loader on user's devices. The purpose of this "malware loader" is to check the user's PC for a minimum amount of kernel threads.
If the infected computer has enough CPU resources, the generic malware loader will download the final payload, the cryptocurrency miner itself.
Trojan used to mine for Monero
According to experts, this trojan is a mixture of various libraries, including parts of the Gh0st RAT, whose parts it uses to communicate with its C&C server and watch the local system. For example, the trojan uses the RAT's features to shut itself down whenever the user launches the Task Manager Windows utility.
To cover a wider target base, the trojan comes with 32-bit and 64-bit versions and uses different configurations based on the available hardware resources.
Crooks use Trojan.BtcMine.1259 to mine for Monero, a cryptocurrency that has slowly replaced Bitcoin in recent years as the de-facto currency used by most cryptocurrency miners. An example of this trend is the EternalMiner malware, a cryptocurrency miner that mines for Monero on Linux servers. EternalMiner was detected last week infecting servers via the SambaCry vulnerability.
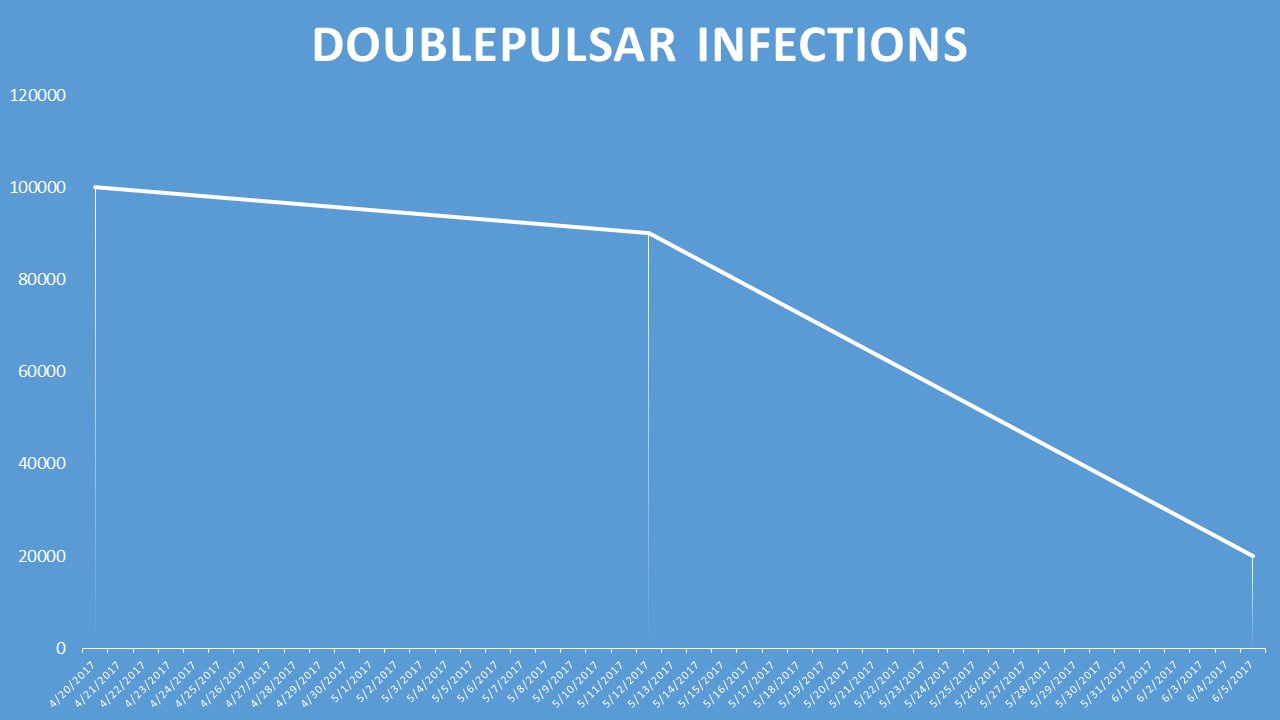
DOUBLEPULSAR infections go down
While many associate DOUBLEPULSAR with the WannaCry ransomware outbreak — where it was used part of the ransomware's self-spreading SMB worm — this malware was deployed in other malware campaigns before.
In April, shortly after the Shadow Brokers dumped the DOUBLEPULSAR implant online, crooks had used it to infect nearly 100,000 computers.
Last week, Shodan founder John Matherly said this number has gone down to just over 16,000 Windows machines. He attributes the decline in numbers to users who updated their systems and applied MS17-010.


Comments
SuperSapien64 - 6 years ago
Another reason I don't feel comfortable surfing the web on Windows.