
A Romanian man and woman are accused of hacking into the outdoor surveillance system deployed by Washington DC police, which they used to distribute ransomware.
The two suspects are named Mihai Alexandru Isvanca and Eveline Cismaru, Romanian nationals, both arrested last week by Romanian authorities part of Operation Bakovia that culminated with the arrest of five suspects on charges of distributing email spam laced with the CTB-Locker and Cerber ransomware strains.
Hackers breached 123 of 187 of Washington police CCTV cameras
According to an affidavit filed by the US Secret Service, the two are accused of hacking into 123 of the 187 security cameras deployed part of the Metropolitan Police Department of the District of Columbia (MPDC) closed-circuit TV system that Washington police uses to keep an eye on public spaces across the city.
Each of these security cameras is controlled "by a dedicated computer installed immediately adjacent to the camera and connected to" MPDC network.
US investigators say Isvanca and Cismaru escalated their access from the security cameras to the adjacent computers. The two allegedly logged in via RDP and started various applications they needed to send spam emails to victims.
The two supposedly hacked MPDC cameras and computers on January 9. Washington police discovered the intrusion on January 12 and shut down the system for four days until January 15 to clean and secure their network.
The shutdown of Washington, DC's entire CCTV system took place two weeks ahead of President Trump's inauguration ceremony and caused a stir in US media, as many initially pinned it on foreign nation-state hackers.
Hacked computer contained a trail of evidence
US Secret Service agents called in to investigate the hack took three of the compromised MPDC computers for further analysis.
Investigators said they found an active infection and apps running on one of these computers. Of all, the most significant was an active browser session for a SendGrid account registered under the name David Andrew (david.andrews2005@gmail.com).
The SendGrid account was being used to send spam emails to 179,616 email addresses contained in a file named USA.txt, found on the compromised computers.
Besides the David Andrew email address, investigators also found that the same computer was also used to access the inbox of anonimano027@gmail.com. After getting access to this account via a warrant, inside this inbox, investigators found several emails of interest to the investigation.
Email accounts linked to one of the suspects
Email communications show that anonimano027@gmail.com received a list of IP addresses, usernames, and passwords from vand.suflete@gmail.com ("vand suflete" means "sell souls" in Romanian). In the list, there were 94 IP addresses belonging to other hacked MPDC surveillance systems.
Another email from the same account referenced a list of IPs, usernames, and passwords for computers infected with the Cerber ransomware. Some IPs were marked with the word "ars," meaning "burnt" in Romanian, while the IP marked with "aici," meaning "here" in Romanian, was the IP of the compromised machine the Secret Service was investigating.
When investigators looked inside the email inbox of the vand.suflete@gmail.com, they said they found a link to the control panel of a Cerber ransomware operation. They also found three emails containing weaponized PDF files that would install the Cerber and Dharma ransomware strains. These files were also hosted on the compromised MPDC systems.
According to the affidavit, US authorities believe Isvanca was behind all three email accounts and has been using all to send data to the compromised WPDC computers.
The clue that led investigators back to Isvanca's true identity was that he used his real-world email address as the recovery email for the anonimano027@gmail.com account.
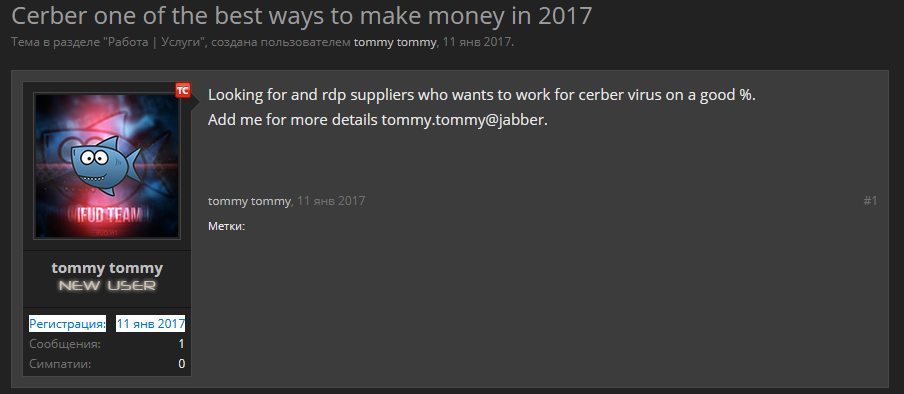
It was this anonimano027@gmail.com email that Isvanca also used to register for an account on the ifud.ws hacking forum, where he published the following ad under the name of "Tommy Tommy":
IP address linked to Isvanca
Furthermore, investigators said that Isvanca used the 86.107.57.138 IP address to register and access all his email accounts, and the same IP was also used to breach a UK healthcare organization's network. The affidavit claims that Isvanca used this organization's servers for his ransomware scheme.
The IP address was later traced to a Romanian Internet provider located in Bucharest. The company, Teen Telecom, supplied authorities with Isvanca's real-world information.
Linking the two suspects together
Authorities connected Isvanca to Cismaru because email account logs that Cismaru used her real-world email address (eveline.cismaru@gmail.com) to send lists of IP addresses to Isvanca's vand.suflete@gmail.com account, from where he forwarded the lists to the anonimano027@gmail.com account that was found on compromised MPDC systems.
Logs also show that Cismaru also sent the USA.txt file to Isvanca's david.andrews2005@gmail.com account, the file used to spam victims with the ransomware-laced PDF files.
US authorities had no difficulty in discovering Cismaru's real-world identity, as she did not use an alias email, and her inbox contained all the information needed to track her whereabouts, including airline bookings, airline tickets, Airbnb account communications, UK driver's license application, and more.
Suspects known to UK and Romanian law enforcement
Both Isvanca and Cismaru are Romanian nationals living in London, UK. At the time of their arrest they were in Romania. According to a source in the threat intelligence community who spoke with your reporter, they were arrested at the Bucharest airport while trying to leave the country.
Romanian law enforcement had also attempted to charge the two on various crimes but had to drop cases due to a lack of evidence.
The US Secret Service doesn't seem to have that problem after seizing and analyzing the hacked MPDC computers. In the affidavit, US investigators tracked down the two suspects down to their Facebook accounts, YouTube profile, passport numbers, government ID numbers, and more.
Isvanca was also included in the UK National Crime Agency's fraud database, where he was "flagged as suspicious due to the fact that the billing address did not match the shipping address."
The affidavit also connected Isvanca and Cismaru to the world of online fraud. Both had exchanged emails that contained thousands of credit card details.
In addition, Isvanca used the david.andrews2005@gmail.com email account to order pizza to an apartment in Bucharest, Romania's capital. According to Romanian authorities, the apartment was registered to Ovidiu Alexandru Dan, a man arrested and charged in 2016 for skimming related crimes. His case is currently pending at a Bucharest court.


Comments
Steve Holle - 6 years ago
Something doesn't make sense here. You can't hack a cctv camera, you can only hack the computer it's connected to. Cctv cameras have to WIFI, no IP address and only send video to whatever they are connected to. If these are WIFI or IP cameras then the aren't CCTV cameras. Two different animals.
nopermission - 6 years ago
is it true what I wrote that hackers are caught behind cerber virus