Security Risk: Dangerous
Exploitation Level: Easy/Remote
DREAD Score: 7/10
Vulnerability: SQL Injection
Patched Version: 1.6.1
As part of our regular research audits for our Sucuri Firewall, we discovered an SQL injection vulnerability affecting 40,000+ users of the Advanced Contact Form 7 DB WordPress plugin.
Current State of the Vulnerability
This plugin saves all Contact Form 7 submissions to the database using a friendly interface. Though the bug has been fixed in the 1.6.1 release, it can be exploited by an attacker who has (at minimum) a subscriber account.
When leveraged, bad actors can leak sensitive data — and in certain configurations compromise an entire WordPress installation.
We are not aware of any exploit attempts currently using this vulnerability.
Disclosure / Response Timeline:
- March 26, 2019: Initial contact attempt.
- April 10, 2019: Patch is live.
Technical Details
WordPress offers an API that enables developers to create content which can be injected to a webpage using a simple shortcode.
The attack vector used to exploit this vulnerability requires the bad actor to have an account on the victim’s site — however, it doesn’t matter what the account privileges are. This is possible thanks to the wp-ajax-parse-media-shortcode function defined in WordPress Core.
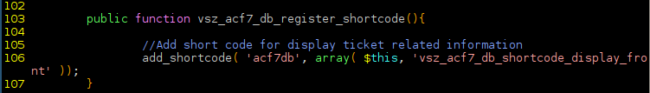
This particular plugin defines the shortcode acf7db in the public/class-advanced-cf7-db-public.php file:
SQL injections can be tricky in the WordPress world due to the increase and popularity of methods like wpdb::prepare, which promise a safe execution of SQL queries.
However, in a number of places user input coming from the shortcode acf7db is not properly sanitized before being included in SQL queries. These queries are then executed directly using the wpdb->get_results() method.
Here is one of the exploitable queries:
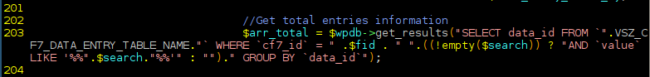
If attackers are able to set arbitrary values for the variable $fid, they can modify the query in such a way that can lead to a full server compromise. We cannot underestimate the ramifications of an SQL injection — or know exactly how many servers may allow attackers to obtain more than just encrypted hashes and user emails.
Indicators of Compromise
While plugin users won’t necessarily see anything malicious on the website, the most obvious indicator of compromise would be malicious content found within the database.
If you begin to see database errors or other unusual behavior and are using a vulnerable version of this plugin, consider patching the vulnerability and scanning your server for malware.
Update as Soon as Possible
SQL injections are dangerous and can impact a variety of SQL databases. Using this vector, attackers can manipulate a site argument in order to inject their own commands to the database and retrieve sensitive data — including usernames and password hashes.
If you’re using a vulnerable version of this plugin, update it immediately to mitigate the risk to your website.
Attacks like the one we see in this particular SQL injection vulnerability are particularly serious. Bad actors can use automation to mount successful, widespread attacks against any website using the vulnerable component.
Keeping your CMS, themes, plugins, and other third-party extensions up to date with the latest patches is a critical element in maintaining a secure website. We encourage plugin users to update to the latest 1.6.1 release as soon as possible.
In the event you are unable to update, we strongly recommend leveraging the Sucuri Firewall or an equivalent technology to virtually patch the vulnerability.