We’ve just announced a major update to iOS Forensic Toolkit, now supporting the full range of devices that can be exploited with the unpatchable checkra1n jailbreak. Why is the checkra1n jailbreak so important for the forensic community, and what new opportunities in acquiring Apple devices does it present to forensic experts? We’ll find out what types of data are available on both AFU (after first unlock) and BFU (before first unlock) devices, discuss the possibilities of acquiring locked iPhones, and provide instructions on installing the checkra1n jailbreak.
checkra1n is not about just the iPhones. We have recently tested checkra1n with Apple TV 4. Today is the day to try the new jailbreak with Apple’s bread-and-butter product, the iPhone. This is not just about supporting the new jailbreak; we’ll try to provide as much useful (and usable) information to LE practitioners as we can about the new exploit, why it cannot be patched by Apple and what the implications are for the future.
Why jailbreak?
We are always asked this question, and I feel it’s worth a good answer. In many cases, jailbreaking is the only gate to all (or most) information available in iOS and tvOS devices. Logical acquisition is a safe and easy way; it always works, and there is nothing to lose. However, logical mostly gives you the same data you can get via the iTunes app: an iTunes-style backup (that may or may not be encrypted), media files and some logs. There’s much more data stored in the iPhone than that, but it does not mean you should skimp on logical. We advise to always do logical first, followed by file system extraction. There’s also the cloud, which you can do at any time.
How checkra1n is different
Jailbreaks always had limited compatibility. Jailbreak releases always lagged behind Apple’s releases, making it possible to jailbreak previous versions of iOS but almost never the current build. The new checkra1n jailbreak supports a wide list of devices and versions of iOS, including many versions of iOS 13. This is also the first jailbreak since the iPhone 4 that can be installed on a “cold” device with an unknown password and then used to extract some data.
Unlike classic jailbreaks such as Chimera or unc0ver, this one is based on a bootrom vulnerability and exploit. checkra1n is potentially compatible with all versions of iOS provided that they run on supported hardware. More importantly, it will remain compatible with new and upcoming iOS releases as the bootrom vulnerability cannot be patched by Apple.
The list of supported devices includes the iPhone 5s, iPhone 6, iPhone SE, iPhone 6s, iPhone 7 and 7 Plus, iPhone 8, 8 Plus and iPhone X, as well as most iPads based on similar SoC. Apple TV HD (ATV4) and Apple TV 4K as well as potentially Apple Watch series 1, 2 and 3 are also in the list.
Supported versions of iOS officially include iOS 12.3 and up, all the way to the current build of iOS 13. Older versions should be supported as well, but have not been tested.
The last time we saw a bootrom exploit of this scale was back in 2010 for the iPhone 4. The limera1n exploit allowed us to be the first who performed a full physical acquisition (true physical, i.e. bit-precise copy of the iPhone storage, passcode cracking, plus the extraction of most of the data without a passcode).
How to install checkra1n
checkra1n is a big departure from the tried and true Cydia Impactor procedure. Which may not be a bad thing since Cydia Impactor has been broken for weeks. The initial version of checkra1n was available for macOS only. Today, there are Windows and Linux versions available. However, the macOS build remains the most reliable, and we still recommend you to use macOS to jailbreak and to perform acquisition, especially if you are doing mobile forensics on a regular basis. If you do not have a Mac yet, it may be a worthy addition to your arsenal. get If you are on a budget, any model that can run macOS Catalina (10.15) will do. While there is a limited set of mobile forensic tools available on the market (apart from our software, we can recommend BlackBag solutions), this is a good investment.
Method 1
Installing checkra1n is quite different from every other jailbreak of the last few years. There is no need to sign and sideload an IPA file to the device. All you have to do is start the checkra1n utility, connect the device (USB-A to Ligning cable is recommended; some sources say that USB-C to Ligtning does not work well) and follow the instructions. The device should be in Normal mode (unless it is locked and the passcode is not known), and the utility first puts it into Recovery mode (automatically), then you have to manually put it into the DFU mode. Honestly, it’s always a pain and just never works from the first try; in the end, with some trial and error, it does. Instructions for various models available here:
Once checkra1n recognizes the device in DFU mode, in installs the jailbreak (it takes just a couple of minutes) and reboots the iPhone. You can now start using iOS Forensic Toolkit.
Method 2 (recommended)
There is an alternative way to install it, and may I say it’s the better way. Even with some (minor) risks involved, we recommend that alternative method instead of the method described above for two reasons:
- No need to enter into Recovery mode first.
- It can be done even for locked devices with unknown passcode.
No GUI time. Just switch the to DFU mode, open the Terminal and run the following commands (note the trailing dash as a parameter in the second command):
cd /checkra1n.app/Contents/MacOS/
./checkra1n_gui -
That’s it, the device is now jailbroken.
Acquisition
Once the jailbreak is installed, start iOS Forensic Toolkit. You can now perform the file system acquisition, exactly the same way you do it with all other jailbreaks. Important: when prompted for the port number, enter 44 instead of the standard 22. The new port number is basically the only difference except for the root password routine. While the root password is still ‘alpine’, the new version of EIFT spares you from the effort of typing it by filling it in automatically. (If the root password was changed, you can still type it manually).
Important: the port number is 44.
There is another important point: if the screen lock passcode is unknown, options D (Disable lock) and K (Keychain) will not be available (throw an error), and only F (File system) works. Besides, if you don’t know the screen lock passcode, only a very limited set of data will be available, see below. To obtain the complete file system (and the keychain), you need to unlock the device, and keep it unlocked during the acquisition.
That’s probably it. The acquisition itself is as simple as that; you will spend most of the time installing the jailbreak (of which getting the device into DFU takes the most effort) and analyzing the results.
With this new jailbreak, can you extract the file system without EIFT or similar software? Technically, you can obtain a copy of the file system. However, you won’t be able to decrypt the keychain. The keychain contains a lot of valuable information such as the user’s credentials for different services ranging from Web sites to social networks and mail accounts, as well as encryption keys for Signal messenger, WhatsApp backups and more.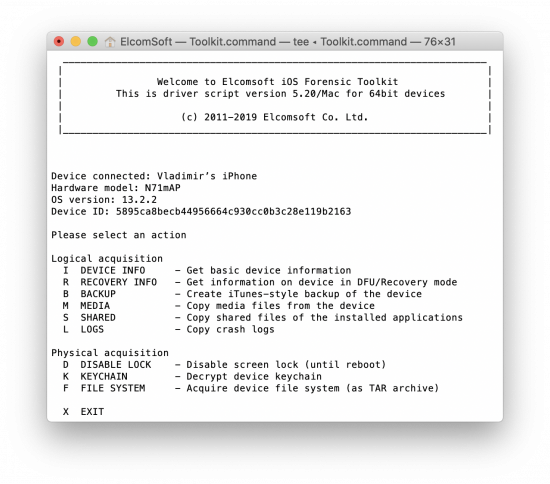
The results
First things first: this jailbreak cannot help with passcode recovery. As we already noted, some limited data can be obtained from locked devices. That’s by design: in iOS, all files may have different protection classes. While the most critical ones are protected with the “when unlocked” attribute (or at least the “after first unlock”), some are available before unlocking. This is necessary for the system to boot, to receive incoming calls (even when the device is just rebooted), process “Find My” requests and more. It does not create a serious security risk as the device itself still remains locked. With the new jailbreak, all such files are accessible prior to unlocking. Just to name some:
Logs, preferences, profiles
- /private/var/installd/Library/Logs/MobileInstallation/
- /private/var/log/
- /private/var/preferences/
- /private/var/root/Library/Preferences/
- /private/var/mobile/Library/Logs/
- /private/var/mobile/Library/Preferences/
- /private/var/mobile/Library/UserConfigurationProfiles/
System databases
- /private/var/wireless/Library/Databases/CellularUsage.db
- /private/var/wireless/Library/Databases/DataUsage.db
- /private/var/root/Library/Caches/locationd/consolidated.db
- /private/var/mobile/Media/Downloads/downloads.28.sqlitedb
- /private/var/mobile/Library/ApplePushService/aps.db
- /private/var/mobile/Library/FrontBoard/applicationState.db
- /private/var/mobile/Library/TCC/TCC.db
Call log and iMessage/SMS (temporary databases)
- /private/var/mobile/Library/CallHistoryDB/CallHistoryTemp.storedata
- /private/var/mobile/Library/SMS/sms-temp.db
Voice mail
- /private/var/mobile/Library/Voicemail/voicemail.db
Have I mentioned the list of accounts (/private/var/mobile/Library/Accounts/Accounts3.sqlite)? No passwords there, yet you can access some information about the device owner and all related accounts used on this device.
You will also get a history of Wi-Fi connections, paired Bluetooth devices, write-ahead logs (WAL) for SQLite databases, WhatsApp *.log files, the list of blocked contacts and dozens various plists; the complete list of non-encrypted files is yet to explore and analyse.
The best results, however, can be achieved only if the device is unlocked (the screen lock passcode is not set or is known). Do not overlook the keychain decryption; you will gain access to tons of passwords and authentication tokens, opening the door for cloud acquisition with Elcomsoft Phone Breaker for Apple iCloud and Elcomsoft Cloud eXplorer for Google accounts.
If you need to analyse a file system image (.tar file), try Elcomsoft Phone Viewer or some of the more advanced forensic packages such as Oxygen Forensic Detective or BlackBag BlackLight (guys, you still need to do a better job analyzing “BFU files”); we cannot trust other tools due to several reasons that are outside the scope of this article.
One more thing
We recently shared some tips on using the iOS Forensic Toolkit on Windows and macOS:
We strongly recommend reading these two articles in order to understand and avoid potential issues (such as the computer connecting to the wrong iOS device). Most importantly (not just for this jailbreak, but in general): before acquisition, disable all Wi-Fi and Ethernet (!) connections on the computer where EIFT is running, and put the iOS device into airplane mode. I cannot stress this enough; if you fail to do this simple thing on BOTH the computer AND the iOS device, all kinds of weird issues may (and probably will) happen.
There is one minor issue with keychain extraction occurring in the Windows edition only. It’s related to the improved SSH connection in the new version (without the need to enter the root password). You will get the following prompt (after selecting the iOS version):
Please select the following action:
1. Forcefully dump keychain without unlocking
2. Wait until device is unlocked and dump keychain after that
In the first case, the Toolkit tries to dump the keychain “as is”, in the current state of the device; only a very limited number of records will be dumped. With the second option, the Toolkit sends a command to unlock the keychain (to receive all the data), and the iPhone shows a prompt to enter the passcode. In that case, you will see Executing… message after unlocking, followed by Press ‘Enter’ to continue once the process is done. The number of extracted records from the particular keychain categories is not printed to console as in the macOS version, but don’t you worry, everything is there.
A word on USB restricted mode and pairing
If you are familiar with USB restricted mode, you may ask whether it affects the ability to jailbreak with checkra1n and acquire with iOS Forensic Toolkit.
The answer is yes, it does. In DFU mode, the device is still accessible even if DFU restricted mode has been activated; checkra1n can be installed and no passcode is needed. Once the jailbreak is installed, partial (BFU) acquisition is possible, and it is worth going after. However, you will still need the screen lock passcode in order to unlock the device and extract the full file system and the keychain.
What about the pairing (lockdown) records? Is it possible to acquire if the device is not paired?
Yes and no. If you work with a device with an unknown passcode, and cannot establish a trusted relationship with the computer, then file system acquisition still works in limited mode. Keychain extraction does not work. We cannot even upload the keychain decryption utility to the device; in order to decrypt the keychain, the device must be unlocked. If the device is unlocked (the passcode is known or not set), you will have to establish a trusted relationship in order to extract and decrypt the keychain.
Acknowledgements
First, many thanks to @axi0mX, the genius researcher who discovered the bootrom vulnerability and created checkm8 exploit. That’s a real breakthrough!
Authors of checkra1n did an excellent job, too! The list of everyone involved in this project is available on their web page. Thanks guys, really appreciated, keep up your good work!
And last but not least, big thanks to Mattia Epifani, a SANS FOR 585 instructor, co-author of Learning iOS Forensics and our good friend. Check his twitter account for up to date information on this topic! Mattia, this work would not be possible without your research, your support and your ideas.
bootrom exploit, chackra1n, ECX, EIFT, Elcomsoft Cloud Explorer, Elcomsoft iOS Forensic Toolkit, Elcomsoft Phone Breaker, Elcomsoft Phone Viewer, EPB, EPPB, EPV, file system acquisition, jailbreak, keychain, physical acquisition



