In May credit reporting service Equifax's website was breached by attackers who eventually made off with Social Security numbers, names, and a dizzying amount of other details for some 145.5 million US consumers. For several hours on Wednesday, and again early Thursday morning, the site was maliciously manipulated again, this time to deliver fraudulent Adobe Flash updates, which when clicked, infected visitors' computers with adware that was detected by only three of 65 antivirus providers.
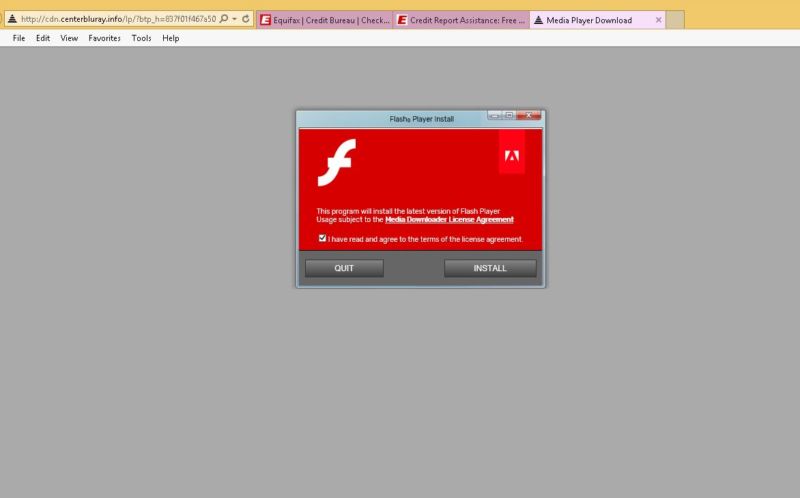
Randy Abrams, an independent security analyst by day, happened to visit the site Wednesday evening to check what he said was false information he had just found on his credit report. Eventually, his browser opened up a page on the domain hxxp//:centerbluray.info that looked like this:
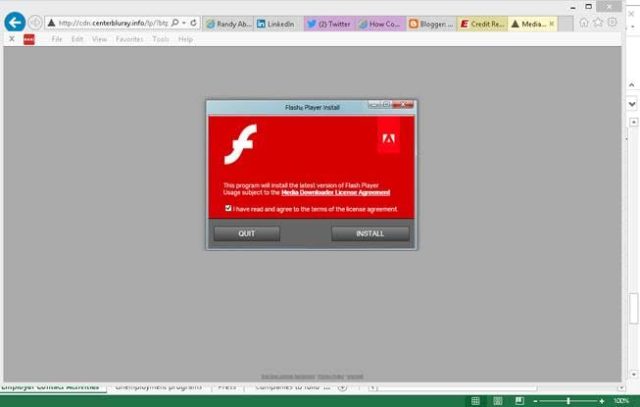
Abrams tried anyway, and to his amazement, he encountered the bogus Flash download links on at least three subsequent visits. The picture above this post is the higher-resolution screenshot he captured during one visit. He also provided the video below. It shows an Equifax page redirecting the browser to at least four domains before finally opening the Flash download at the same centerbluray.info page.
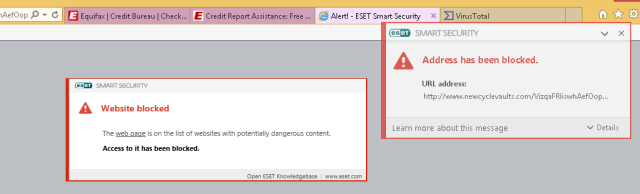
The file that got delivered when Abrams clicked through is called MediaDownloaderIron.exe. This VirusTotal entry shows only Panda, Symantec, and Webroot detecting the file as adware. This separate malware analysis from Payload Security shows the code is highly obfuscated and takes pains to conceal itself from reverse engineering. Malwarebytes flagged the centerbluray.info site as one that pushes malware, while both Eset and Avira provided similar malware warnings for one of the intermediate domains, newcyclevaults.com.
Malvertising, analytics?
It's not yet clear precisely how the Flash download page got displayed. The group-sourced analysis here and this independent assessment from researcher Kevin Beaumont—both submitted in the hours after this post went live—make a strong case that Equifax was working with a third-party ad network or analytics provider that's responsible for the redirects. In that case, the breach, technically speaking, isn't on the Equifax website and may be affecting other sites as well. But even if that's true, the net result is that the Equifax site was arguably compromised in some way, since administrators couldn't control the pages visitors saw when trying to use key functions, some which require visitors to enter Social Security numbers.
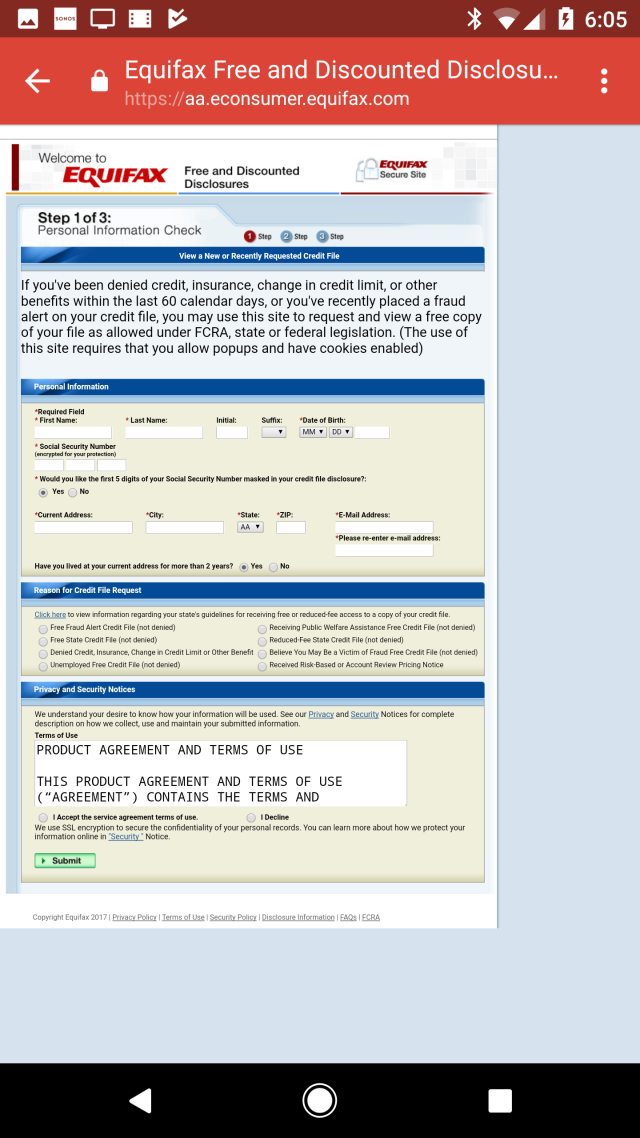
Several hours after this post went live, an Ars reader e-mailed to say he recently encountered a sketchy ad when putting a temporary fraud alert on his Equifax file. The reader wrote:
When I clicked it (from Gmail on Android) I was redirected to a spam page shortly after seeing the Equifax credit file form. I thought maybe it was an anomaly because it didn't happen again. But after reading your article about how sometimes hacks will redirect randomly I tried the link again just now and sure enough I got a spam page again (lucksupply.club saying I won an iPhone X). This is Chrome-in-a-tab from Gmail so i don't believe there's any extensions or other malware on my device that could have caused this redirect.
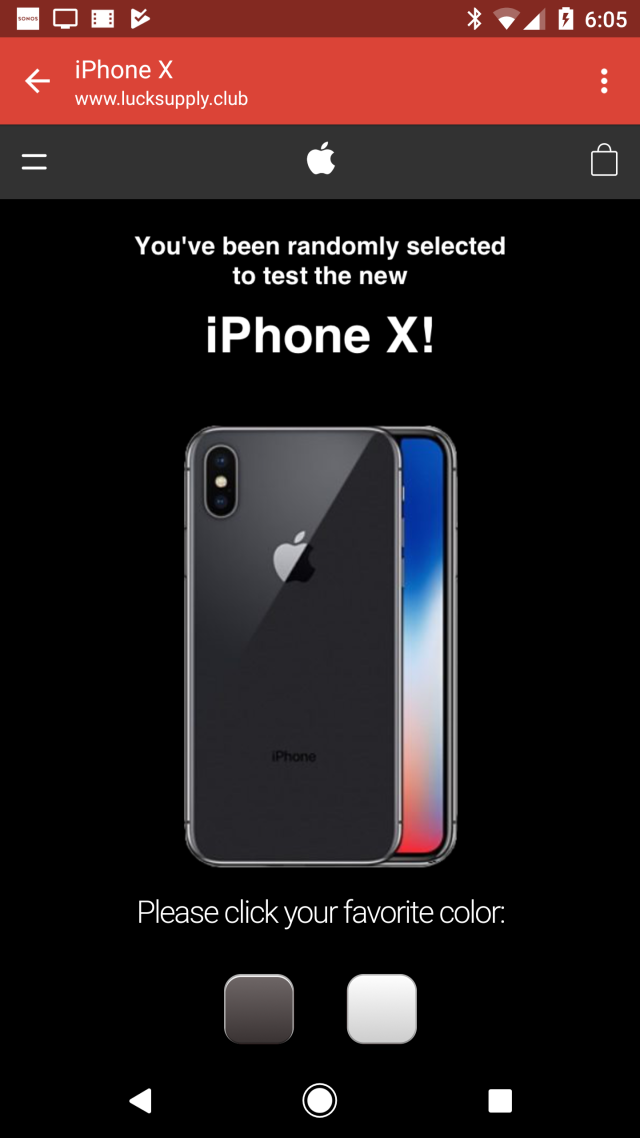
In the hour this post was being reported and written, Abrams was unable to reproduce the redirects leading to the malicious download, but he said they returned early Thursday morning. Shortly after that, a section of the site was taken down. In an e-mail sent mid Thursday morning, an Equifax represesentative wrote:
We are aware of the situation identified on the equifax.com website in the credit report assistance link. Our IT and Security teams are looking into this matter, and out of an abundance of caution have temporarily taken this page offline. When it becomes available or we have more information to share, we will.
Post updated at several times on the morning of 10/12/2017 Pacific time to discuss ad networks and add details of ad served on reader. The word "hacked" was removed from the headline to reflect the possibility the redirects are the result of a third-party malvertising campaign.
reader comments
147