In an era when new consumer data breaches are disclosed daily, fake claims about data leaks are sadly becoming more common. These claims typically come from fame-seeking youngsters who enjoy trolling journalists and corporations, and otherwise wasting everyone’s time. Fortunately, a new analysis of recent bogus breach claims provides some simple tools that anyone can use to quickly identify fake data leak claims.
 The following scenario plays out far too often. E-fame seekers post a fake database dump to a site like Pastebin and begin messaging journalists on Twitter and other social networks, claiming that the dump is “proof” that a particular company has been hacked. Inevitably, some media outlets will post stories questioning whether the company was indeed hacked, and the damage has been done.
The following scenario plays out far too often. E-fame seekers post a fake database dump to a site like Pastebin and begin messaging journalists on Twitter and other social networks, claiming that the dump is “proof” that a particular company has been hacked. Inevitably, some media outlets will post stories questioning whether the company was indeed hacked, and the damage has been done.
Fortunately, there are some basic steps that companies, journalists and regular folk can take to quickly test whether a claimed data leak is at all valid, while reducing unwarranted damage to reputation caused by media frenzy and public concern. The fact-checking tips come in a paper from Allison Nixon, a researcher with Deloitte who — for nearly the past two years — has been my go-to person for vetting public data breach claims.
According to Nixon, the easiest way to check a leak claim is to run a simple online search for several of its components. As Nixon explains, seeking out unique-looking artifacts — such as odd passwords or email addresses — very often reveals that the supposed leak is in fact little more than a recycled leak from months or years prior. While this may seem like an obvious tip, it’s appalling at how often reporters fail to take even this basic step in fact-checking a breach claim.
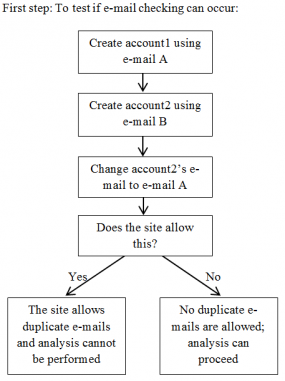
A somewhat more advanced test seeks to measure how many of the “leaked” accounts are already registered at the supposedly breached organization. Most online services do not allow two different user accounts to have the same email address, so attempting to sign up for an account using an email address in the claimed leak data is an effective way to test leak claims. If several of the email addresses in the claimed leak list do not already have accounts associated with them at the allegedly breached Web site, the claim is almost certainly bogus.
To determine whether the alleged victim site requires email uniqueness for user accounts, the following test should work: Create two different accounts at the service, each using unique email addresses. Then attempt to change one of the account’s email address to the others. If the site disallows that change, no duplicate emails are allowed, and the analysis can proceed.
Importantly, Nixon notes that these techniques only demonstrate a leak is fake — not that a compromise has or hasn’t occurred. One of the sneakier ways that ne’er-do-wells produce convincing data leak claims is through the use of what’s called a “combolist.” With combolists, miscreants will try to build lists of legitimate credentials from a specific site using public lists of credentials from previous leaks at other sites.
This technique works because a fair percentage of users re-use passwords at multiple sites. Armed with various account-checking programs, e-fame seekers can quickly build a list of working credential pairs for any number of sites, and use that information to back up claims that the site has been hacked.
But according to Nixon, there are some basic patterns that appear in lists of credentials that are essentially culled from combolists.
“Very often, you can tell a list of credentials is from a combolist because the list will be nothing more than username and password pairs, instead of password hashes and a whole bunch of other database information,” Nixon said.
A great example of this came earlier this month when multiple media outlets repeated a hacker’s claim that he’d stolen a database of almost seven million Dropbox login credentials. The author of that hoax claimed he would release on Pastebin more snippets of Dropbox account credentials as he received additional donations to his Bitcoin account. Dropbox later put up a blog post stating that the usernames and passwords posted in that “leak” were likely stolen from other services.
Other ways of vetting a claimed leak involve more detailed and time-intensive research, such as researching the online history of the hacker who’s making the leak claims.
“If you look at the motivation, it’s mostly ego-driven,” Nixon said. “They want to be a famous hacker. If they have a handle attached to the claim — a name they’ve used before — that tells me that they want a reputation, but that also means I can check their history to see if they have posted fake leaks in the past. If I see a political manifesto at the top of a list of credentials, that tells me that the suspected leak is more about the message and the ego than any sort of breach disclosure.”
Nixon said while attackers can use the techniques contained in her paper to produce higher quality fake leaks, the awareness provided by the document will provide a greater overall benefit to the public than to the attackers alone.
“For the most part, there are a few fake breaches that get posted over and over again on Pastebin,” she said. “There is just a ton of background noise, and I would say only a tiny percentage of these breach claims are legitimate.”
A full copy of the Deloitte report is available here (PDF).




So um, yeah…isn’t the recycling of old credentials the same thing your buddy Alex Holden did, and you ran with the story AND vouched for him on the legitimacy of the “hack” he found by the Russians. This post by you is the pot calling the kettle black. Come on Brian, you’re better than that.
The irony in this article is quite amazing, isn’t it?
Apples, oranges. Not the same thing at all.
Alex’s data has always been solid, and he is one of the good guys. But his approach with that disclosure was off-putting and not terribly well thought-out.
Seriously? Let’s for arguments sake say BK knew the story was fake before running it, the (hypothetical) “worst” way BK could have behaved as a journalist.
I would still have to say what has that got to do with this story. It’s not even as though BK has gone after anyone else in the media for the seeming lack of very basic fact checking when God knows he would’ve been justified doing it?
But that isn’t what happened at all is it … apples and oranges is about right.
It was not the story that rankled people, it was vouching for Holden.
Well, that’s too bad. I still vouch for him, even if he did ignore all my advice prior to launching that project.
For better or worse, there is a fine line between selling security services and selling fear, uncertainty and doubt. And talented security researchers can cross that line pretty easily if they don’t have a lot of experience interacting with the community as a whole. Also, the security community tends to have a long memory for perceived infractions of these unwritten rules.
The fine line between selling FUD and anything is all too often crossed by those who want an increasing share of a diminishing supply of “attention”, a critical element. By sowing FUD so frequently, citizens become numb to real dangers. The worst thing about compromised information is its growing acceptance as inevitable and commonplace.
Numb minds, deliberately induced or not, has led to an electorate in which barely half who can, actually do, vote. The result is a 51% winner has the support of one-half of one-half. Or: 3 out of 4 didn’t vote for them. “Reality tv” does not help and we need better. Otherwise the real dangers are on the short side of the decreasing signal to noise ratio.
Of course that is just my opinion, I could be wrong (Thx DM)
Jonathan @nc3mobi
Interesting. I note that both the New York Times and the Wall Street Journal today both credit Mr. Holden’s reports with tipping investigators off to the JP Morgan breach.
http://www.nasdaq.com/article/jp-morgan-found-hackers-after-finding-breach-of-race-website–2nd-update-20141031-00745
http://dealbook.nytimes.com/2014/10/31/discovery-of-jpmorgan-cyberattack-aided-by-company-that-runs-race-website-for-bank/?partner=rss&emc=rss
Judging by some screenshots and other hints in some tech articles it’s fairly obvious that it’s common practice for journalists and bloggers to try logging into the accounts listed in a password dumps in order to verify that the passwords are correct.
I’ve a feeling that this article will become the authoritative reference for journalists, so might be worth explicitly stating that this isn’t a good idea.
“If I see a political manifesto at the top of a list of credentials, that tells me that the suspected leak is more about the message and THE EGO than any sort of breach disclosure.”
Having a cause = Have ego
go figure
True hackers don’t hack for a cause, they either hack for the joy of hacking… or hack to get paid.
If you see someone championing a cause, it probably means they’re a script kiddy who likes to pretend they’re a hacker. My niece is not a hacker, even if she downloads LOIC. Hackers don’t think their computer hates them just because their battery won’t hold a charge.
Julian Assange hacks (or hacked) for a cause.
I’m sure I could just begin with the circles he frequents to find many other examples that apparently aren’t “true hackers” according to you.
Might I suggest that the reasons why you are doing something don’t have anything at all to do with being a hacker much like the reasons why I ride a bicycle don’t have anything to do with whether I’m a cyclist or not.
We need a new term for the profiteers and criminals that besmirched the good name of “hacking”. Hacking used to be just exploring and learning how to make stupid computer programs do things they are not originally designed to do. Which if you were ever a programmer was entirely entertaining. If you have never programmed or even written a little script in VB you can’t enjoy the fun as much.
Blackhats are all egotistical smarmy bigheads with no appreciation for the underlying technology they abuse. They do not respect anything or anyone who disagrees with them. They do not care who they hurt or how much pain they cause. Profit or no I can’t refer to them as hackers.
There is a difference.
Another vote for having unique passwords for each site you log into. Yes, its annoying. And maybe even inconvenient. But so is having a breach at one online site compromise your credentials at ALL the online sites you visit.
You can already do this sort of using Canary (disclaimer: my service).
A perfect example is of the number of “hacks” claimed by different parties against the FBI:
https://canary.pw/view/?item=2b2dbddf26aefd425ddd40c32216617a
Using the ‘related’ tab, you can see all the copycats.
that’s a nice singing canary you have there. so what else can it do? I have a dog, Outside of a dog, a book is a man’s best friend. Inside of a dog it’s too dark to read..
Canary is actually an awesome tool. Journos, take note.
Interesting article, and I’m very glad for the report, thank you.
I do think your comment “it’s appalling at how often reporters fail to take even this basic step in fact-checking” inadvertently swerves into the reality that is the media today, and maybe has always been the case for the majority of media outlets.
I think instead of spending a few minutes researching a leak, which could be fake and therefore a waste of time, is worthless for reporters. Really, who wants to read a story about someone faking a breach (aside from us ;-).
Comparing the reporter who learns the breach is fake, and ignores it, to the reporter who doesn’t care, and runs with the story as if it were real, I’d be willing to bet that the site carrying the breach report “as real” receives more views than the site who ignored it.
Further I’d wonder about the negative impact on the reporter who didn’t run the breach story “as real” versus the reporter who did run it as real. My guess would be that there is zero negative impact for the reporter whose article generated views, and that the reporter who didn’t generate views, is likely in some hot water.
I might be persuaded to believe that reporters are as unconcerned with the (for lack of better phrase) victims of their reporting as they are concerned with their own paycheck. e.g. So what if people leave Dropbox, I still have a job, and in two weeks everyone will forget anyway.
I might also be persuaded that this will not change.
I might be persuaded that you’re entirely correct. “Integrity” has never been a word that universally applies to the profession of news reporting, a fact that its denizens have not remedied by re-branding their profession as “journalism”.
Liars are still liars, by any other name.
Politics is the art of looking for trouble, finding it everywhere, diagnosing it incorrectly and applying the wrong remedies.
This also applies to Journalism and Teleprompter reading
Sadly, crime seems to be a virtue now. The average person is undoubtedly not going to be able to keep up with it all and sooner rather than later, will fall to some criminal act which they may never be able to recover from.
Crooks know old habits die hard. They see the majority of the world doing the same thing, the same basic way and are taking advantage of the masses.
So you can either be a part of that mass, waiting for the so-called inevitable, dire disaster that may ensue, or
You can cut the cord and think out of the box and protect yourself from these crimes. Most of the crimes have to reach pretty long in order for them to get to you.
So to cut them off.
Put a credit freeze on your accounts
Pay with cash only. Bills can be paid via your bank for a very small fee.
Have credit monitoring for about 12 bucks a month for a year or two after you transition over. make sure once credit monitoring is in place you opt out of any solicitations coming from the credit agency, and that can be done for up to 5 years online.
Sure it may be a pain in the rear to adjust, but taking away some of the simplistic things can burn the bridge between you and the crooks over time.
I refuse to accept, refuse to give in and refuse to drop my guard when it comes to crooks. Empower a different way of thinking, rather than accepting “eventual defeat.”
Sure you aren’t looking at the attackers making the heist by getting journalists to say it was hacked, then they get discredited, and all the while the public, HR machinery, and IT are all chewed up in the process of fighting each other, the actual breech happens? Then when someone says a breech has happened, they call wolf.
Also, anyone with half a brain would have a way of verifying a dump. Mr Krebs has a an e-mail at a local bank to verify the credit data and checking account logins for validity is such a basic, trivial thing to do.
pah, back in my day we had to write our checkers ourself…..
You still should, since the criminals you “buy” the software from will subsequently attempt to steal your identity, accounts, etc.
There is no honor among thieves.
Nope…only thievery and more thievery (plus some one-upsmanship, too)!
Another good way is to find correct and accurate information about security breaches is to sign up to reputable security website newsletters, like Security Breach Daily.
so what’s the link? the only one i see is http://www.databreachtoday.com/
Thanks to Ms. Nixon & BK for making this available. For years I’ve been tracking breaches for the NC3 project and unsubscribed from many a “source” because the material provided was akin to Monty Python’s Spammity Spam, an ancestor for the title of BK’s book.
For those of you feeling nostalgic
http://www.youtube.com/watch?v=XZ6N5m8FpVg
3m 23s
Jonathan @nc3mobi
Still don’t take this worthy reporting an kill the messenger, we will have nothing to read with our morning coffee. But, with the gutting of the reporter staff at newspapers comes consequences. Less time. Time where the science staff, could check out a story. Time where other reporters could consult on “what do I do next?”‘ After all, look at what has become of the ” better papers” mere shells of themselves, instead of delivering the news, making the news, becoming stars, not reporters.
Yep, oranges and apples. Several sites pumping the same basic info about breach notifications;
http://www.csoonline.com/article/2840901/security/how-to-figure-out-if-a-data-breach-is-a-hoax.html#tk.rss_news
I’m SO sorry, guys – I know your community has it’s squabbles, as it should – but I am just an ordinary citizen and information is important to us. _That’s_ what this site is really about. INFORMATION (how to protect yourself, where the “bad guys” are focusing, where the weaknesses in the current system(s) are, etc.)
So a HUGE THANK YOU!!!
Why has the page layout changed since yesterday? Today the site looks like it was slapped together by someone who’s just learned HTML and has no knowledge at all of bgcolor, font, and other presentation tags, to say nothing of CSS.
It was much more professional-looking (and laid out to be easier to read when displayed on wide screens) until sometime yesterday or this morning.
Looks okay to me, but you may be seeing the remnants of some mitigation on DDoS attacks that have been hitting the site pretty much non-stop of late. I bet if you accessed the site via another IP you would a much different result.
The site’s layout looks the same as usual to me, even the date is that non-standard way that Brian likes it.
Maybe the DDOS attack finished? I hope so. Attacks waste bandwidth, which wastes electricity, which wastes fuel I could be buying at a lower price to save at the pump, which would let me buy an extra snack.
Lesson: DDOS attacks take snacks out of my mouth. 🙁
You don’t say which browser you were using, but I have seen webpages from Yahoo mis-rendered by Firefox. It’s like the browser fully displays the html portion without any of the CSS or javascript. Usually the other elements finish loading, or the browser finishes interpreting the CSS and javascript, and the page transforms to its correct appearance. Sometimes the page fails to change and I have to reload the webpage.
I figure the page-rendering fails on sites like Yahoo is because the webpages are complex and have several javascripts running, some of them several hundred kilobytes in size, as well as scripts within the Flash-animated advertising.
Since I disable all JS, Flash, and other client-side Turing-complete executable material on all sites save for a selective whitelist, I don’t tend to have that problem. 😉
Why would mitigation affect the site’s layout?
not to mention any patches from your favorite operating system that also may affect your browser… add in Flash, Java and all the other things that could affect your view.
if you have an alternate system, fire that one up and compare the site…and the software loaded and patch levels.
Issues are not always on the other end.
Perhaps my hosting provider put up Nginx for a spell. That has been known to cause problems with the CSS. In any case, are you still having the problem?
No. What is Nginx?
http://lmgtfy.com/?q=nginx+wikipedia
Here’s what I don’t get – why can’t credit cards use a two factor authentication app like online services do? I have an app that continuously generates new codes for Google, Lastpass, etc. Why can’t we do that with credit and debit cards?
Arguably any research that is not performed in conjuction with the breached company is just scam-dvertising. Here’s why http://bit.ly/1yNGwi9
Alex Trican wrote on Secradar dot com Security Blog:
“The bottom line is that this type of research should only be done from within the company affected by the breach(and their hired researchers) and then presented to journalists as a fact, as opposed to writing speculations for the sake of media coverage.”
Alex, you may be missing a few significant points:
The company affected may not know they were breached. How many breaches were unknown to be breached until an INDEPENDENT security researcher puts together the pieces? Most companies do not want their security weaknesses to be publicized. It took LEGISLATION to force some disclosures. The exception and model for disclosure was K-Mart/SHD who detected a breach internally on 10/9, made an SEC disclosure the same day, and went public starting with a press release the next day. Compare that to months or even years for other companies who delayed while consumers continued to be damaged by crooks.
Taking that to an extreme: If companies were required to only disclose when they wanted to we may never know how many times our confidential consumer credentials were compromised. We’d just get new cards and dispute charges and continue to have our credit scores dinged and linked debit accounts drained.
Lastly, this is the Land of the Free, made so because it is also the Home of the Brave. There is a reason that Freedom of the Press is mentioned in the FIRST of our Bill of Rights. It protects us from not being able to look behind the curtain to see that the Wizard is just a man. That some do a poor job, or pervert the power of the press for poor purposes, is a sadness to be certain, but Independent Security Researchers are for the public good, and working pro bono publico helps protect us when we have to be very aware from whom we buy. CAVEAT EMPTOR! Sic Transit Gloria Mundi or Tuesday will be worse (especially this Tuesday).
I already voted. Did you?
Jonathan @nc3mobi
Thanks for going after the truth and protecting consumers.
Sometimes I get the feeling there is something in it for the card issuer to have their technology pilfered by hackers and thieves, yet all our common sense would say otherwise. They seem neither motivated to upgrade technology nor active in enforcing security measures.
And it seems US card giants are the main culprits of this ‘agnostic’ attitude towards better technology and methods of enforcing it. Its like they profit somehow from the underground activity of their systems. Money laundering etc.
Am I the only one that thinks/suspects this?
It just seems there are straight out more scecure systems in todays day an age than ‘signatures’ and ‘cc numbers’, ‘tap n go’ etc.
It stinks of something.