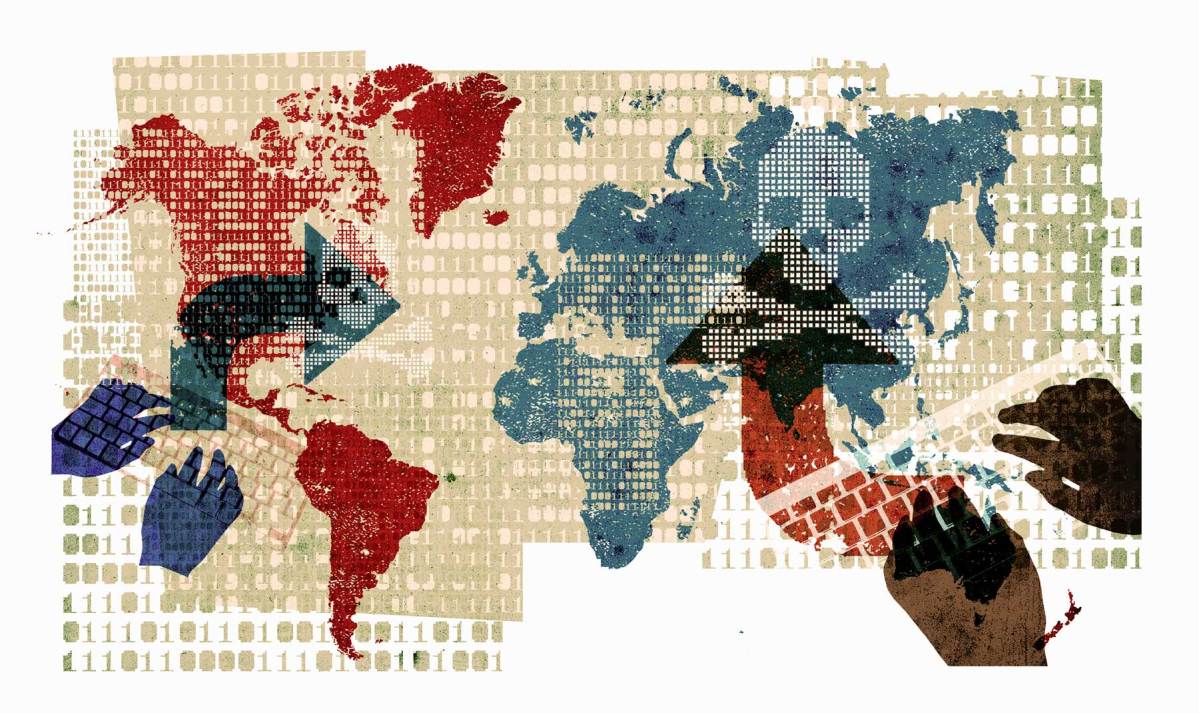
Two waves of widespread cyberattacks shut down computer systems from India to the United States in the last two months. CBS News reported the costs in damages from the so-called WannaCry attack in May alone may reach a staggering $4 billion.
And despite the scale of the incursions, cybersecurity experts think the worst is yet to come.
In late June, governments and organizations scrambled to recover their data after it was essentially held hostage. The malware, dubbed “NotPetya,” froze their computers and encrypted their hard drives, which was promised to be undone if a sum money was paid in Bitcoin, a popular kind of digital currency. At first glance, the attack resembled a kind of cyberattack known as ransomware and echoed the WannaCry attack a month earlier.
Ransomware attacks are “low hanging fruit” for hackers, according to Edward Stroz, co-president of cybersecurity firm Stroz Friedberg. The former FBI agent told RealClearLife that these kinds of attacks are fairly easy to carry out and a quick way to score some cash.
Those without a hacking background can find ready-to-deploy ransomware on the deep and dark web, alongside digital mercenaries for hire to help carry out the attack. Some hackers with business savvy even developed ransom-paying interfaces that are more intuitive than some software applications, Stroz says. “The link between a need or a desire to do something like this and the facility to be able to implement it has never been a shorter distance,” he added.
Unlike other cyberattacks that utilize unknown security flaws called “zero-day exploits,” ransomware often uses well-known vulnerabilities and preys on people that neglect to download software updates from Microsoft or Apple. In the case of NotPetya and Wannacry, both used a vulnerability called EternalBlue, an exploit previously used by the NSA to hack into computers undetected—until it was leaked by a hacktivist group known as the Shadow Brokers.
Found in Windows operating systems, the EternalBlue exploit allows for malware to spread to devices sharing the same network. The vulnerability was fixed by Microsoft before the WannaCry attack in May, but it still managed to infect hundreds of thousands of computers which didn’t have the software update installed. Meanwhile, NotPetya infected just 12,000 computers, according to Microsoft.
Unlike WannaCry, IBM Security Researcher Wendi Whitmore says that NotPetya was able to utilize the EternalBlue vulnerability even if computers have downloaded the Microsoft software update. So if more devices were vulnerable to NotPetya than to WannaCry, why were fewer computers affected? The hackers responsible for NotPetya may not have actually been after money.
“This recent Petya variant was not ransomware, but instead a wiper disguised as ransomware. Unlike ransomware, wiper malware is designed to destroy systems and data; the attacker offers no option for recovery,” Whitmore explained in a recent Quora post.

The ransom was likely only asked in order to throw investigators off the trail. NotPetya’s sophistication undermined by techniques that would’ve limited its profits. In fact, there’s growing evidence to suggest that NotPetya’s ransomware-like appearance was a ruse to distraction from the real target: Ukraine. According to Kaspersky Lab, about 60 percent of the infected computer networks were Ukrainian and most belonged to state-operated services, like banks and public transportation.
NATO says the sophisticated approach indicates the work of a nation or state-sponsored hackers. Ukraine has already blamed Russia for the clever cyberattack, as the superpower already has a history of meddling in its neighbor’s computer networks, according to Wired. However, Ed Stroz thinks there should be a lot more caution when making claims of attribution—especially when it comes to pointing the finger at countries like Russia or North Korea, which is under suspicion for the WannaCry attack.
“I’d really want to make sure that the circumstantial evidence for attribution is really strong,” Stroz said. He compared investigating cyberattacks to an Agatha Christie mystery, in which the assumed suspect is actually innocent and the true culprit is revealed in the investigation’s final moments. Hackers can leave a trail of digital breadcrumbs that can mislead forensic investigators. “An adversary may want to make it look like its coming from a country in the penalty box and it might not be.”
Whether a state-sponsored or independent attack, ransomware is so attractive that cybercriminals raked in $1 billion in 2016 from the method, according to one researcher’s estimate. “It is so easy for a small spark, one person with a match, to create an enormous impact when the conditions are right,” Stroz said, comparing it digital arson.
WannaCry froze up hospital systems across Britain, and as alarming as that may be, Stroz says the recent spate of attacks should serve as a wake-up call. “The vulnerability and the impact can be quite large, even with a small group if they put some effort into it,” he explained. “I don’t think we’ve ever faced a challenge by adversaries that can be described that way.”
The good news is there is a way to prevent ransomware attacks from being so destructive.”If you’re hit by this, the effect doesn’t have to be that bad,” Stroz explained. “Why don’t we do what we can to reduce the vulnerability?”
That starts with “good cyber hygiene” as Stroz calls it, which boils down to being smart about opening files from unrecognized emails and basic cybersecurity measures. “If something does get through our protections, let’s minimize the impact,” he says.
In the case of ransomware, an isolated hard drive that regularly backed up can control the damage. “If you have that ability to recover from the drive that has been encrypted,” Stroz explained. Even in the case of NotPetya, which didn’t prevented decrypting hard drives, this is a viable solution.
Whatever the motivation might be—whether it’s causing mayhem, stealing money, or sending a message—NotPetya could be the beginning of ransomware being wielded in unexpected ways. However, Stroz says one thing can be expected: more ransomware attacks. “Who would bet against the dark side of human nature that we aren’t going to see this again?”
This article was featured in the InsideHook newsletter. Sign up now.