Network Visibility Products
Garland Technology ensures complete packet visibility by delivering a full platform of network TAP (test access point), inline bypass and packet broker products.
Visibility Solutions
Garland Technology is committed to educating the benefits of having a strong foundation of network visibility and access. By providing this insight we protect the security of data across your network and beyond.
Resources
Garland Technology's resource library offers free use of white papers, eBooks, use cases, infographics, data sheets, video demos and more.
Blog
The TAP into Technology blog provides the latest news and insights on network access and visibility, including: network security, network monitoring and appliance connectivity and guest blogs from Industry experts and technology partners
Partners
Our extensive technology partnership ecosystem solves critical problems when it comes to network security, monitoring, application analysis, forensics and packet inspection.
Company
Garland Technology is dedicated to high standards in quality and reliability, while delivering the greatest economical solutions for enterprise, service providers, and government agencies worldwide.
Contact
Whether you are ready to make a network TAP your foundation of visibility or just have questions, please contact us. Ask us about the Garland Difference!
How Much is My Information Worth on the Dark Web?

In the April 5, 2016 report by the Identity Threat Resourse Center (ITRC) there have been 227 breaches which have compromised 6,214,514 records containing personally identifiable information (PII). The ITRC tracks data breaches involving social security numbers, credit/debit card numbers, email/password/username records and protected health information (PHI).
It’s no secret this information is the new currency on the Dark Web. But let’s identify the how’s and why’s - and then what to do to avoid your information - both as an individual and as an organization from getting hacked.
How is Data Compromised?
Most of the studies indicate that data was acquired by insiders, aka: trusted environments that have physical devices like computers, tablets, phones, skimming devices, PoS, etc. How easy is it to en masse this data? One key logger on a Point-of-Sale (PoS) device can gather thousands of files before they are found out. ATM skimmers and cameras that record your credit card data accompanied by cameras recording your password on just a few ATMs will collect hundreds, of credit card numbers which will immediately be sold on the dark web.
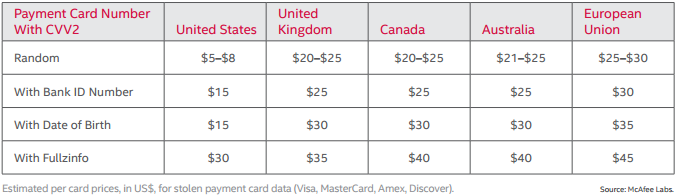
Where is my Data Being Sold and What Cost?
Most stolen data is being sold in the Dark Web. But for how much? Here’s what the recent McAfee’s report, Hidden Data Economy estimates:
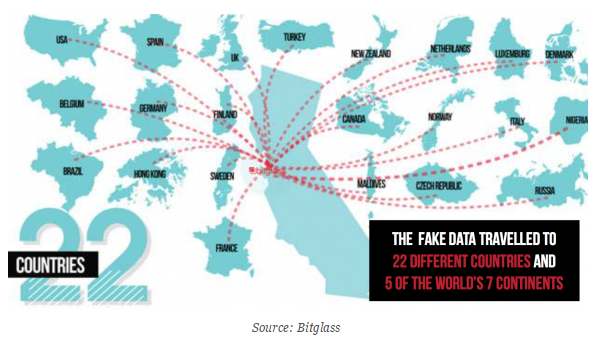
Bitglass, undertook an experiment in 2015 to understand what happens to sensitive data once it’s stolen. In the experiment, stolen data traveled the globe, landing in five different continents and 22 countries within two weeks. Overall, the data was viewed more than 1,000 times and downloaded 47 times; some activity had connections to crime syndicates in Nigeria and Russia.
I hope you are gasping. My intent is to horrify you. We cannot become complacent about being hacked. Just because your new credit card is over-nighted to you doesn’t mean there aren’t real life consequences for stolen data.
In 2015 over half of American adults had their personal information exposed - for those of us in this bucket (including me), it’s inconvenient, especially if you need to to recover your credit standing or regain your identity and not to mention the minor annoyances of auto renewal payments on Pandora, EZ-Pass, Netflix, etc. that will haunt you for 30+ days.
Loyalty Programs to Enhance Profiling
It’s not just credit card information for sale. On the Dark Web just about any information can be found, including free online accounts, including loyalty programs.
What’s the value? At face value, maybe it’s for the reward points. Digging deeper maybe it’s to profile targets of interest. Let me scare you a bit more. Let’s pretend we are watching Black List and Red needs to find and interrogate a U.S. Congressman. He can build an accurate profile by compiling data from the following loyalty programs: airline and hotel, gas and convenient store, Uber and Amtrak, fast food and coffee houses, and retail programs.
By having a key identifier, ie. personal email, Red knows, “Congressman Joe goes to Starbucks, corner of East and West everyday, orders a double espresso and then hops on Amtrak #7 Eastbound. He also goes to Subway for lunch between 2-3pm, corner of Smith and Weston. Every Sunday he stays home and binge watches Downton Abbey.”
Loyalty programs without an e-commerce component are an easy target to hack because they may not even use encryption. Simple child’s play in a hacker’s world.
Avoidance of a Hack is Impractical; But Use Your Best Defenses:
On the Human Side:
- Use a shredder - for everything: CDs, invoices, solicitations, etc.
- Change your passwords monthly
- Use random passwords with letters, numbers and special characters
- Use two factor authentication when offered
- Only trust your information to encrypted (https://) websites
- Turn technology off when it’s not being used
- Unplug when you are away for more than a day
- Be smart about smart technology - do you really need wifi on your garage door? Does your refrigerator need to communicate with you?
- Pick up the phone and verify legitimate business partners
- Be wary of wire transfer requests and invoice urgency emails
- Don’t open emails from unknown senders
- Don’t open attachments you are not expecting
- Don’t click on embedded links in emails
On the Technology Side:
- Cyber security is more than a firewall and antivirus software
- Defend the perimeter, use monitoring software to see unusual activity
- Train for the human-factor
- Know your baseline traffic
Be vigilant and keep watch of your finances, but not while while you’re using the free wifi at the coffee shop.
Be Safe – The Oldcommguy®
P.S. If your like me and don't click embedded links, here are the links to cut and paste in your browser:
http://www.idtheftcenter.org/images/breach/DataBreachReports_2016.pdf
https://blog.malwarebytes.org/cybercrime/2013/05/atm-and-point-of-sale-terminals-malware-the-bad-guys-just-never-stop/
http://www.mcafee.com/us/resources/reports/rp-hidden-data-economy.pdf
http://www.bitglass.com/
http://www.bitglass.com/company/news/press_releases/bitglasswheresyourdata
https://www.garlandtechnology.com/blog/slash-the-cost-of-a-security-breach-within-your-network
http://www.nytimes.com/interactive/2015/07/29/technology/personaltech/what-parts-of-your-information-have-been-exposed-to-hackers-quiz.html?_r=0
http://www.nbc.com/the-blacklist
https://www.garlandtechnology.com/blog/protect-your-network-know-your-baseline-traffic
Written by Tim O'Neill
As the Senior Technology Consultant & Chief Editor at LoveMyTool, Tim O’Neill has over 45 years of technology experience at data/voice and video networking analysis companies, including successful senior roles in Sales, Product Design, Marketing Management, Business Development and Security.
Authors
Topics
- IT Security (200)
- Network TAPs (138)
- Network Monitoring (133)
- Hacks and Breaches (87)
- Network Management (77)
- Network Design (73)
- Industrial OT (70)
- Technology Partners (63)
- Network Infrastructure (56)
- Inline Security (49)
- TAPs vs SPAN (47)
- Network Packet Brokers (40)
- Data Center (37)
- Cloud Solutions (33)
- Software Defined Networking (SDN) (24)
- Events & News (20)
- The 101 Series (18)
- Federal (17)
- Cisco Solutions (16)
- Wireshark (14)
- DesignIT (13)
- Healthcare (11)
- MSP/MSSP (9)
- Palo Alto Networks (8)
- Finance (7)
- Troubleshooting (5)
